Category: HelpnetSecurity
Here’s a look at the most interesting products from the past week, featuring releases from Brivo, Envoy, Prove, Rubrik, and…
A surge in brute-force attempts targeting Fortinet SSL VPNs that was spotted earlier this month could be a portent of…
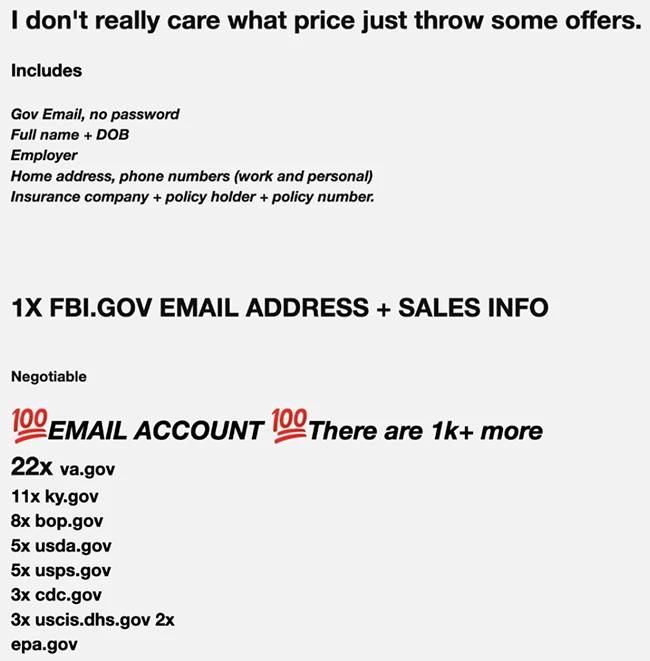
Active police and government email accounts are being sold on the dark web for as little as $40, giving cybercriminals…
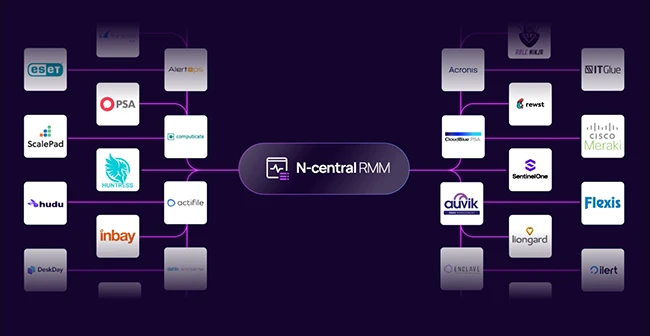
Two vulnerabilities (CVE-2025-8875, CVE-2025-8876) in N-central, a remote monitoring and management (RMM) solution by N-able that’s popular with managed service…
Brivo a strategic partnership with Envoy. The integration brings Envoy’s workplace platform, designed to connect people, spaces, and data, into…
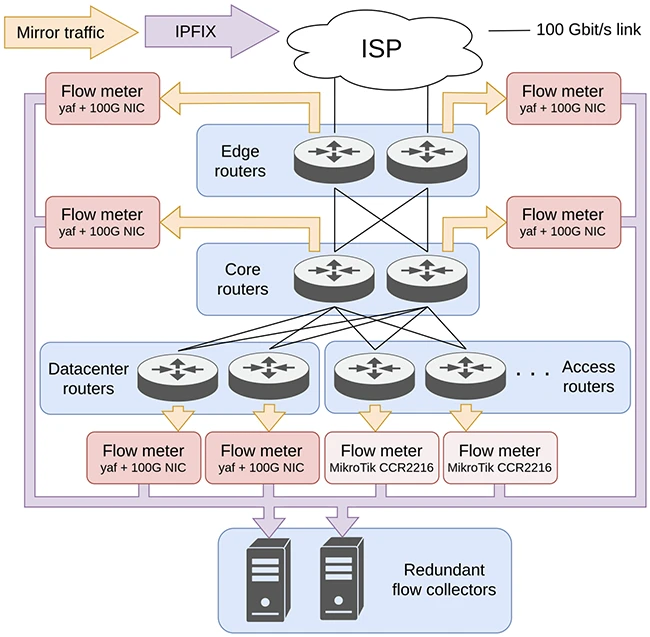
Flow monitoring tools are useful for tracking traffic patterns, planning capacity, and spotting threats. But many off-the-shelf solutions come with…
Learn how AI technologies can be applied to enhance security, create safe and responsible applications, develop intelligent agents, and improve…
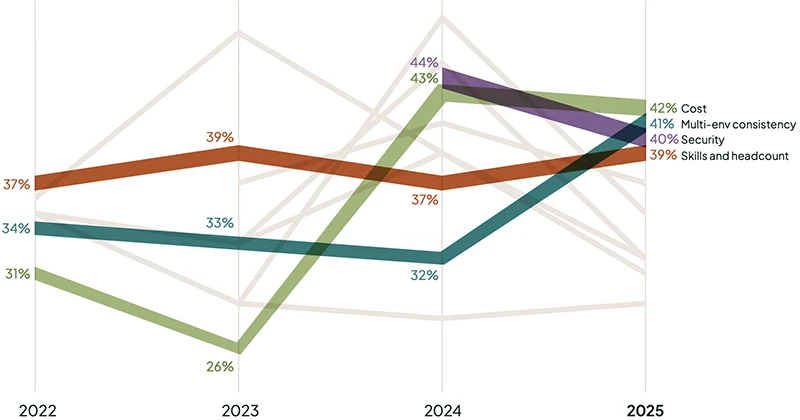
AI is changing how enterprises approach Kubernetes operations, strategy, and scale. The 2025 State of Production Kubernetes report from Spectro…
The Ruđer Bošković Institute (RBI), the largest Croatian science and technology research institute, has confirmed that it was the one…
The National Institute of Standards and Technology (NIST) has finalized a lightweight cryptography standard to protect even the smallest networked…
For August 2025 Patch Tuesday, Microsoft has released security updates resolving 100+ security vulnerabilities in its various solutions, including a…
Fortinet has released patches for a critical OS command injection vulnerability (CVE-2025-25256) in FortiSIEM, after practical exploit code surfaced in…