Category: HelpnetSecurity
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Review: LLM Engineer’s HandbookFor all…
In this Help Net Security interview, Rohan Sen, Principal, Cyber, Data, and Tech Risk, PwC US, discusses how organizations can…
A cyberattack on a water facility can put entire communities and businesses at risk. Even a short disruption in clean…
CISA Certified Information Systems Auditor Practice Tests offers practical, domain-by-domain prep for the CISA exam, with hundreds of questions covering…
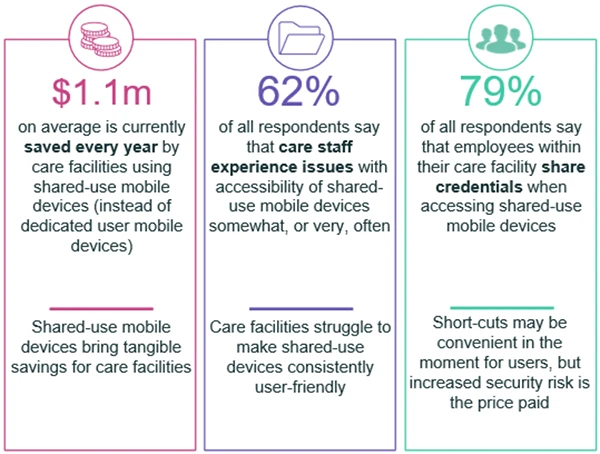
Shared mobile devices are becoming the standard in hospitals and health systems. While they offer cost savings and workflow improvements,…
Here’s a look at the most interesting products from the past month, featuring releases from: Akeyless, At-Bay, Barracuda Networks, Bitdefender,…
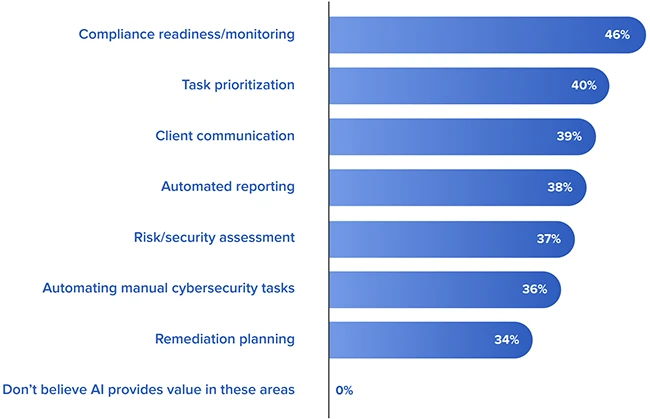
Virtual CISO (vCISO) services have moved from niche to mainstream, with vCISO services adoption 2025 data showing a more than…
A team of researchers has developed a new AI model, called White-Basilisk, that detects software vulnerabilities more efficiently than much…
Secrets like API keys, tokens, and credentials are scattered across messaging apps, spreadsheets, CI/CD logs, and even support tickets. According…
Cyber threats are becoming more frequent and sophisticated, and rural hospitals and clinics are feeling the pressure from all sides:…
Identity-based attack paths are behind most breaches today, yet many organizations can’t actually see how those paths form. The 2025…
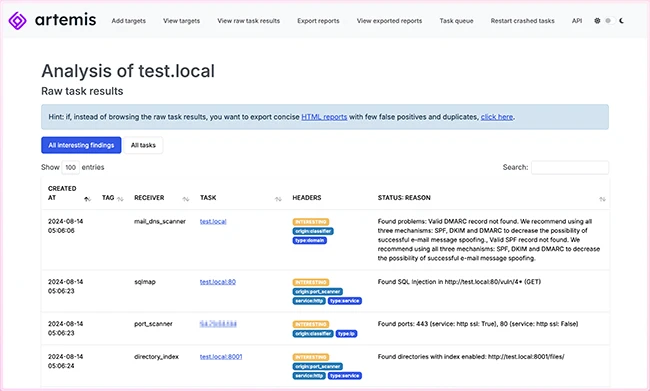
Artemis is an open-source modular vulnerability scanner that checks different aspects of a website’s security and translates the results into…