Category: HelpnetSecurity
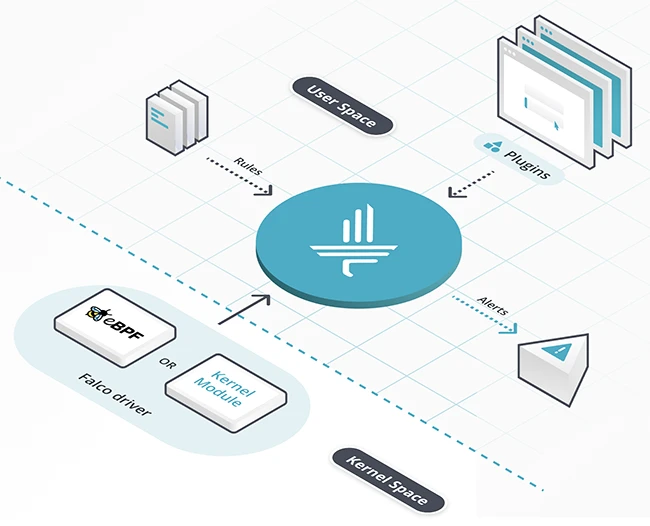
Falco is an open-source runtime security tool for Linux systems, built for cloud-native environments. It monitors the system in real…
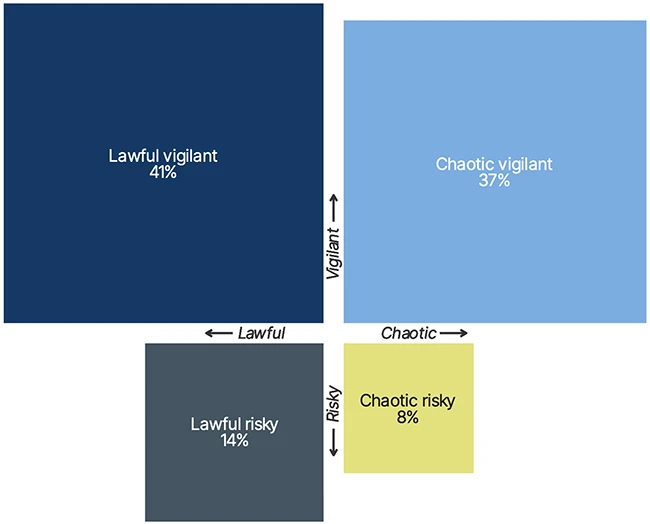
A new report from Living Security and the Cyentia Institute sheds light on the real human element behind cybersecurity threats,…
UEFI firmware running on 100+ Gigabyte motherboard models is affected by memory corruption vulnerabilities that may allow attackers to install…
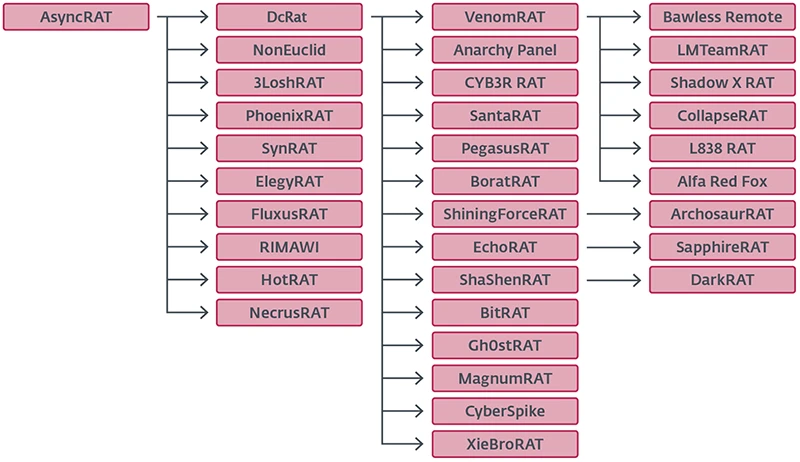
AsyncRAT is an open-source remote access trojan that first appeared on GitHub in 2019. It includes a range of typical…
In this Help Net Security interview, Robert Knoblauch, CISO at Element Fleet Management, discusses how the rise of connected vehicles…
For decades, manufacturers and security professionals have been playing a high-stakes game of cat and mouse with counterfeiters. From holograms…
A growing number of MSPs, MSSPs, and consultancies are moving beyond one-and-done engagements and transforming from tactical vendors into strategic…
After every breach, people ask: How did this happen if there were cybersecurity policies in place? The truth is, just…
Application Penetration Tester Tata Consultancy Services | Ireland | Hybrid – View job details As an Application Penetration Tester, you…
MITRE has introduced AADAPT (Adversarial Actions in Digital Asset Payment Technologies), a new cybersecurity framework designed to tackle vulnerabilities in…
With two proof-of-concept (PoC) exploits made public late last week, CVE-2025-25257 – a critical SQL command injection vulnerability in Fortinet’s…
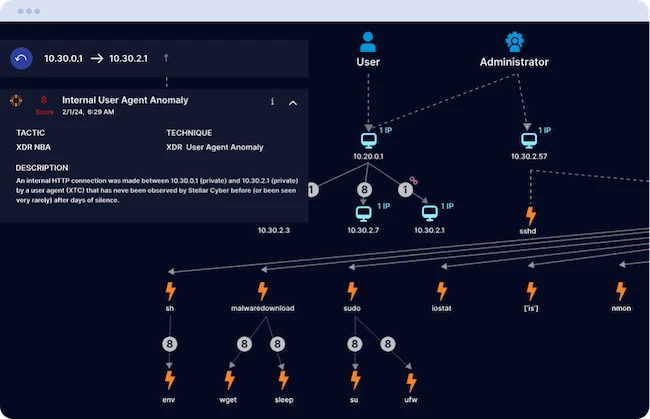
Stellar Cyber released version 6.0.0 of its award-winning open and unified SecOps Platform, introducing new AI-driven capabilities and workflow enhancements…