Category: HelpnetSecurity
Four individuals suspected of having been involved in the ransomware attacks that hit UK-based retailers earlier this year have been…
Claroty researcher Noam Moshe has discovered serious vulnerabilities in two Ruckus Networks (formerly Ruckus Wireless) products that may allow attackers…
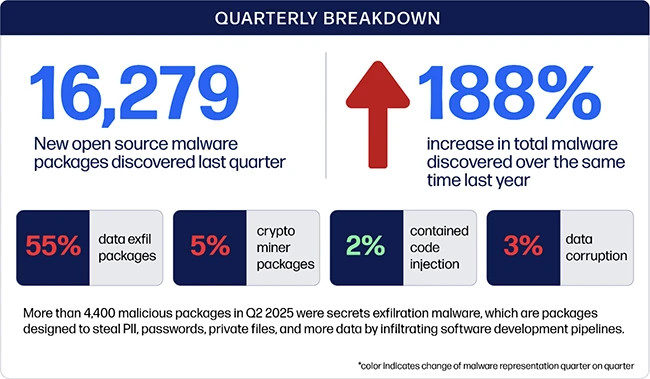
Sonatype has published its Q2 2025 Open Source Malware Index, identifying 16,279 malicious open source packages across major ecosystems such…
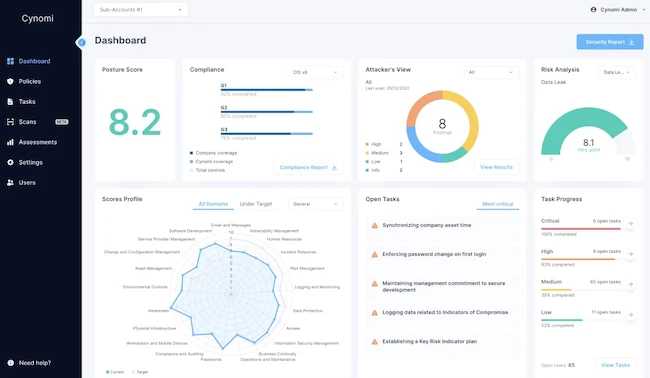
Cynomi has launched new business impact analysis (BIA) and business continuity planning (BCP) features. Designed to help cybersecurity professionals identify…
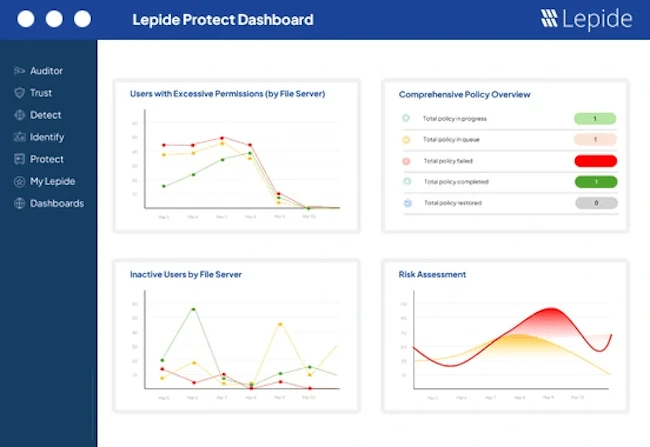
In a move set to redefine the way organizations manage data access and implement zero trust, Lepide launched Lepide Protect, an…
In this Help Net Security interview, David Warburton, Director at F5 Labs, discusses how the EU’s Post-Quantum Cryptography (PQC) roadmap…
Shopping on a fake online store can lead to more than a bad purchase. It could mean losing money, having…
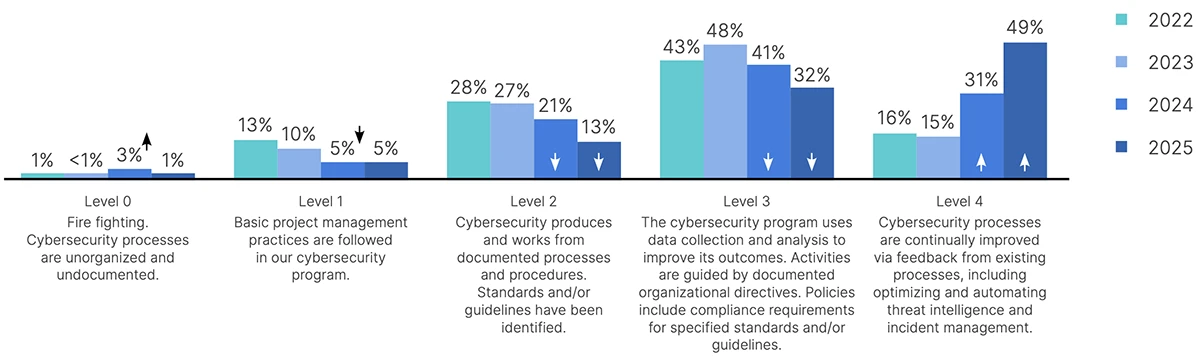
There has been a significant increase in the global trend of corporations planning to integrate cybersecurity under the CISO or…
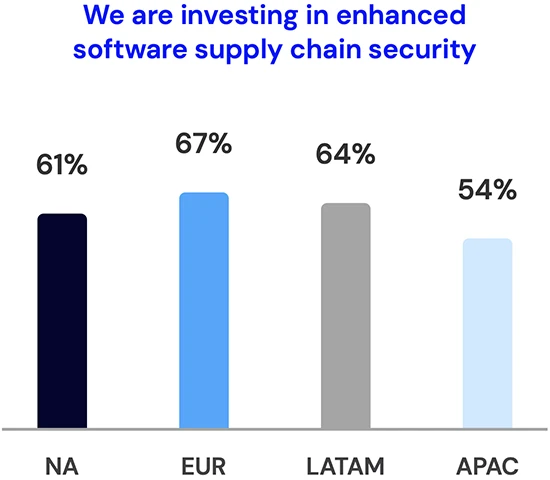
Only 23% of organizations are confident that they have very high visibility of their software supply chain, according to LevelBlue’s…
For July 2025 Patch Tuesday, Microsoft has released patches for 130 vulnerabilities, among them one that’s publicly disclosed (CVE-2025-49719) and…
In this Help Net Security interview, Dr. Nicole Nichols, Distinguished Engineer in Machine Learning Security at Palo Alto Networks, discusses…
Cybersecurity friction usually gets framed as a user problem: password policies that frustrate employees, MFA that slows down logins, or…