Category: HelpnetSecurity
Aegis Authenticator is an open-source 2FA app for Android that helps you manage login codes for your online accounts. The…
Attack Surface Management (ASM) has become one of those buzzwords that gets used a lot but rarely explained in detail….
While most enterprises have integrated cloud resources into their operations, many need to improve their ability to secure these environments…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Sudo local privilege escalation vulnerabilities…
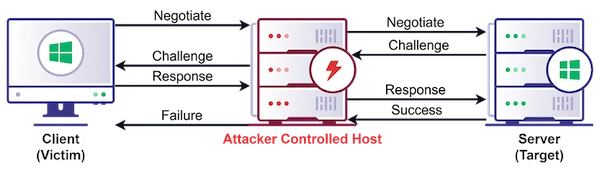
NTLM relay attacks are the easiest way for an attacker to compromise domain-joined hosts. While many security practitioners think NTLM…
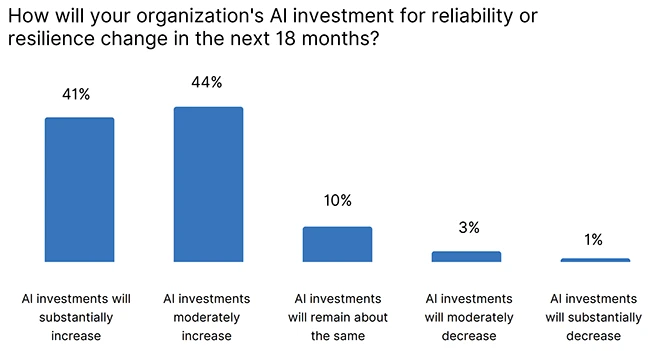
To ensure resilience across the internet stack, organizations need to protect and manage four key areas: reachability, availability, reliability, and…
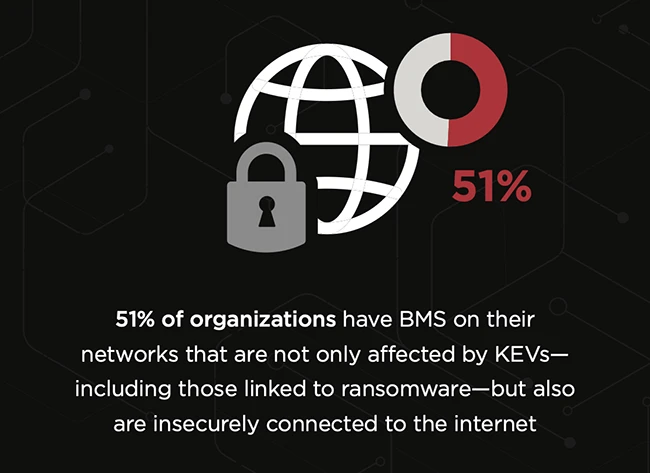
75% of organizations have building management systems (BMS) affected by known exploited vulnerabilities (KEVs), according to Claroty. Threats to building…
Here’s a look at the most interesting products from the past week, featuring releases from DigitalOcean, Scamnetic, StealthCores, and Tracer…
Age verification is becoming more common across websites and online services. But many current methods require users to share personal…
Popular AI chatbots powered by large language models (LLMs) often fail to provide accurate information on any topic, but researchers…
Cisco has found a backdoor account in yet another of its software solutions: CVE-2025-20309, stemming from default credentials for the…
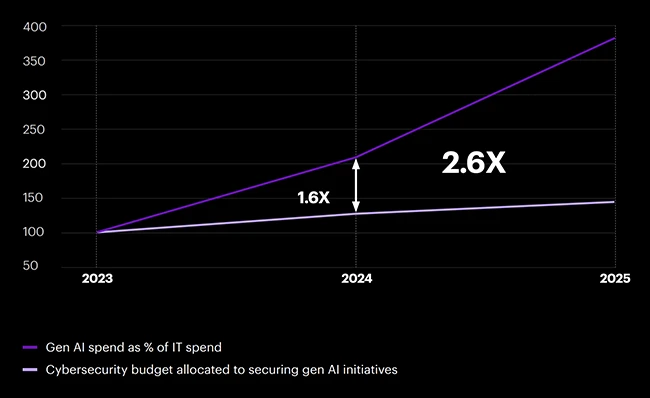
As AI reshapes business, 90% of organizations are not adequately prepared to secure their AI-driven future, according to a new…