Category: HelpnetSecurity
Insider threats are among the hardest attacks to detect because they come from people who already have legitimate access. Security…
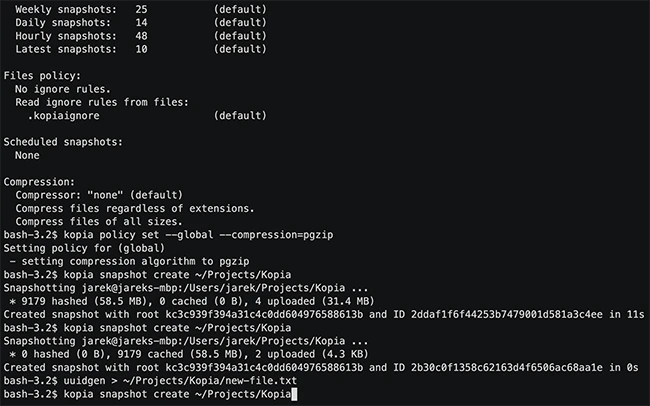
Kopia is an open-source backup and restore tool that lets you create encrypted snapshots of your files and store them…
Adversarial AI Attacks, Mitigations, and Defense Strategies shows how AI systems can be attacked and how defenders can prepare. It’s…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Android VPN apps used by…
In its recently released 2025 Threat Hunting Report, Crowdstrike pointed out an interesting trend: a 136% surge in cloud intrusions….
Authorities in Africa have arrested 1,209 people in an Interpol-led crackdown on cybercrime that targeted nearly 88,000 victims. 11,432 malicious…
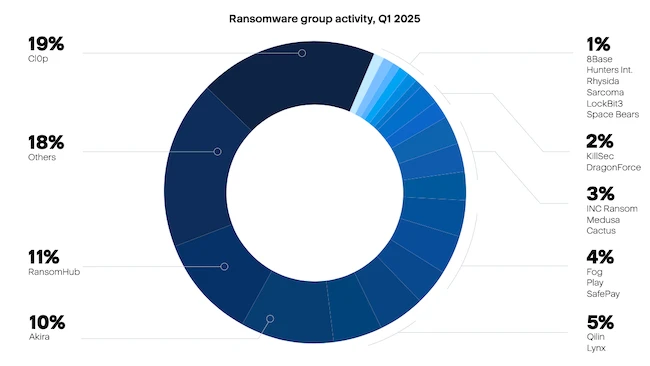
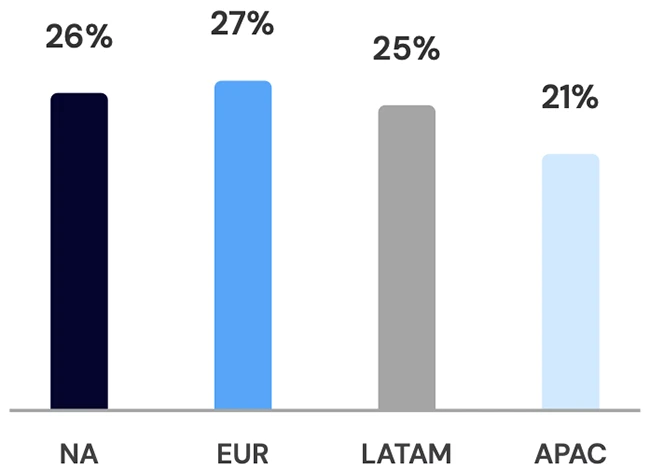
Ransomware continues to be the major threat to large and medium-sized businesses, with numerous ransomware gangs abusing AI for automation,…
Attackers don’t always need a technical flaw. More often, they just trick your people. Social engineering works, and AI makes…
A small-town water system, a county hospital, and a local school district may not seem like front-line targets in global…
Here’s a look at the most interesting products from the past week, featuring releases from Doppel, Druva, LastPass, and StackHawk….
A threat group linked to the Russian Federal Security Service’s (FSB) Center 16 unit has been compromising unpatched and end-of-life…
AWS’s Trusted Advisor tool, which is supposed to warn customers if their (cloud) S3 storage buckets are publicly exposed, could…