Category: HelpnetSecurity
Cloud adoption is speeding ahead in the business services sector, but security for remote and edge environments is falling behind….
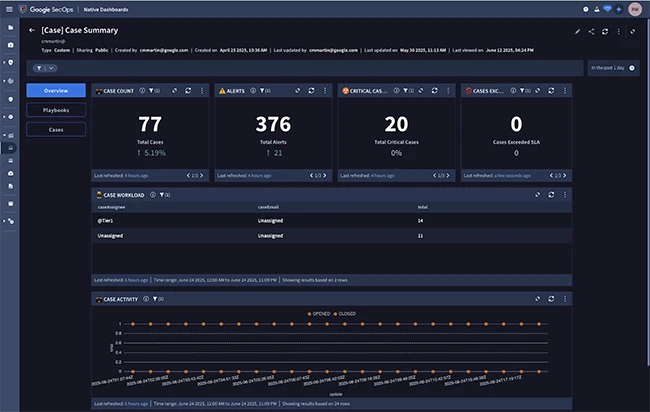
Google used its Cloud Security Summit 2025 today to introduce a wide range of updates aimed at securing AI innovation…
The lines between SaaS and AI are vanishing. AI agents are now first-class citizens in your SaaS universe: accessing sensitive…
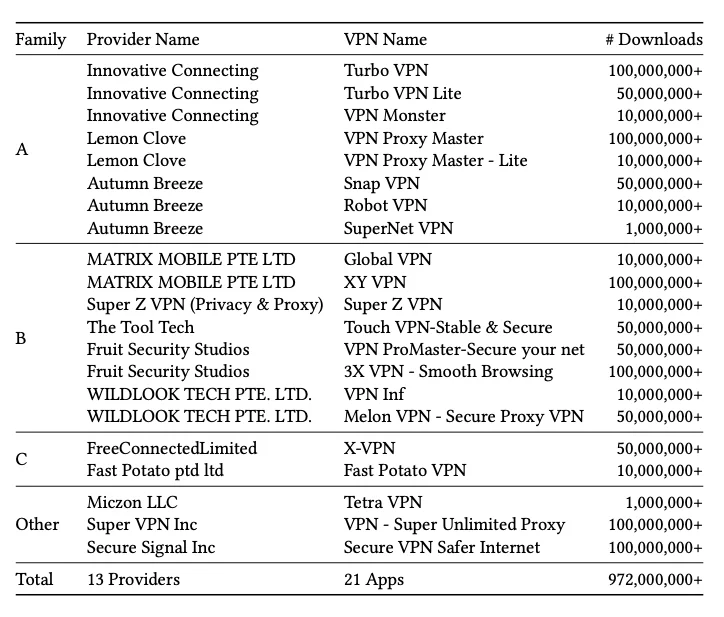
Three families of Android VPN apps, with a combined 700 million-plus Google Play downloads, are secretly linked, according to a…
Cybersecurity training often struggles to match the complexity of threats. A new approach combining digital twins and LLMs aims to…
Git 2.51 is out, and the release continues the long process of modernizing the version control system. The update includes…
Cybersecurity myths are like digital weeds: pull one out, and another quickly sprouts in its place. You’ve probably heard them…
Senior Cybersecurity Analyst DOT Security | USA | On-site – View job details As a Senior Cybersecurity Analyst, you will…
Face morphing software can blend two people’s photos into one image, making it possible for someone to fool identity checks…
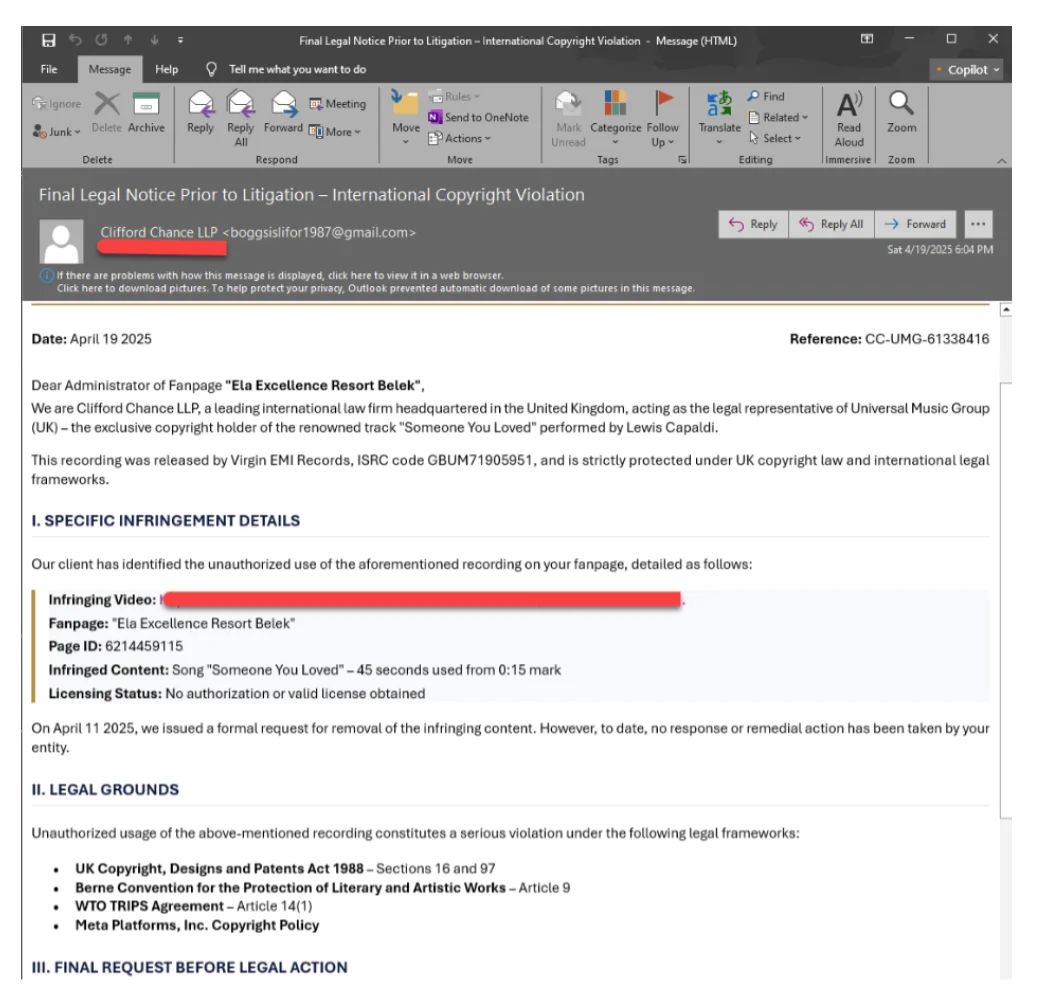
Attackers pushing the Noodlophile infostealer are targeting businesses with spear-phishing emails threatening legal action due to copyright or intellectual property…
Data Engineering for Cybersecurity sets out to bridge a gap many security teams encounter: knowing what to do with the…
AI is moving from proof-of-concept into everyday security operations. In many SOCs, it is now used to cut down alert…