Category: HelpnetSecurity
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Black Hat USA 2025Black Hat…
July turned into a surprisingly busy month. It started slowly with a fairly ‘calm’ Patch Tuesday as I forecasted in…
Over a third of companies say they are using AI, including generative AI, to fight fraud, according to Experian. As…
Cybercriminals are getting better at lying. That’s the takeaway from a new LevelBlue report, which outlines how attackers are using…
Here’s a look at the most interesting products from the past week, featuring releases from Black Kite, Descope, Elastic, ExtraHop,…
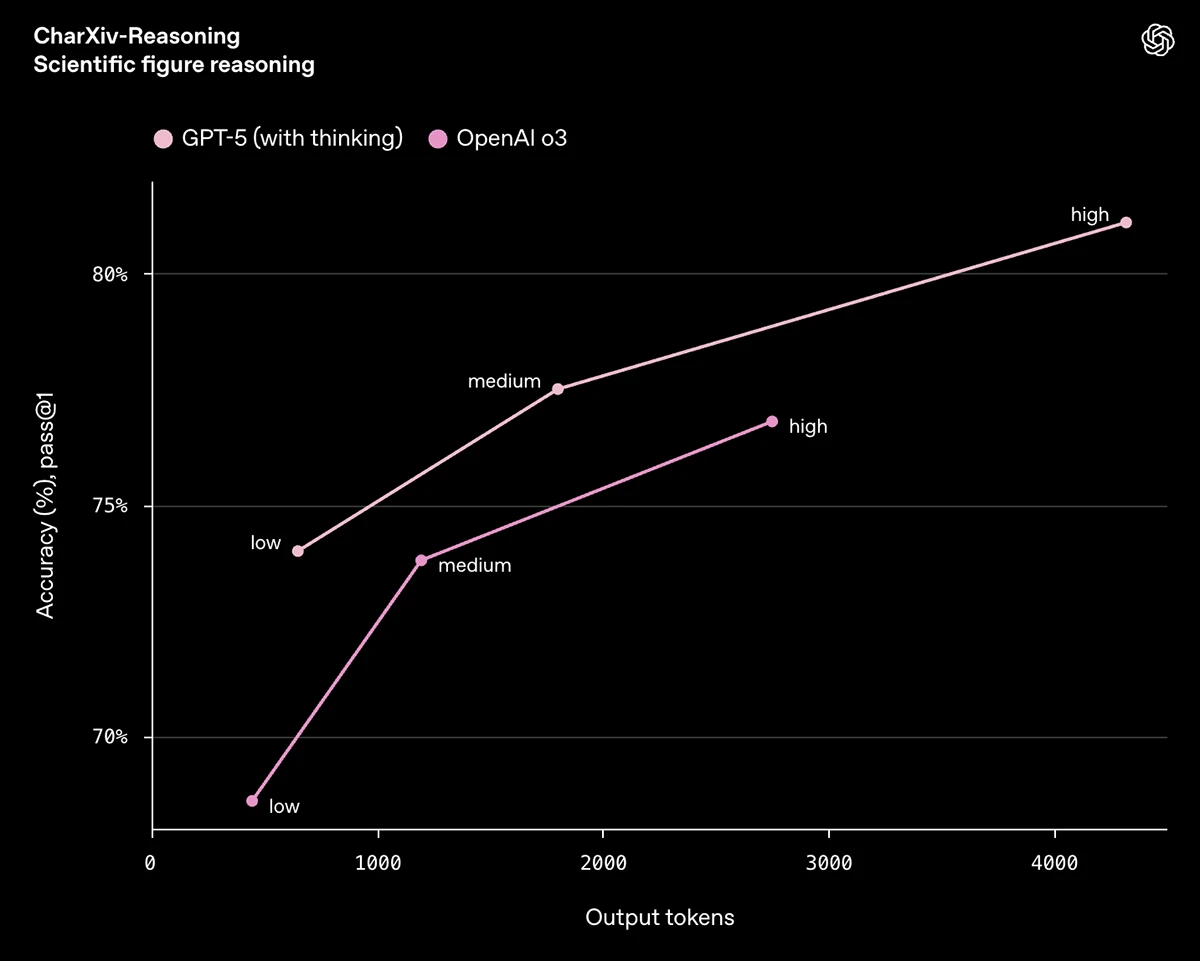
OpenAI has released GPT‑5, the newest version of its large language model. It’s now available to developers and ChatGPT users,…
“In an Exchange hybrid deployment, an attacker who first gains administrative access to an on-premises Exchange server could potentially escalate…
Akira ransomware affiliates are not leveraging an unknown, zero-day vulnerability in SonicWall Gen 7 firewalls to breach corporate networks, the…
Black Hat USA 2025 was packed with innovation, with companies showing off tools built to get ahead of what’s coming…
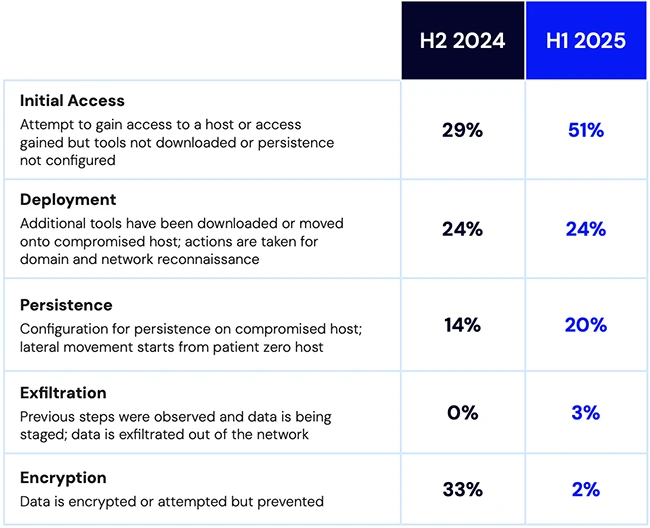
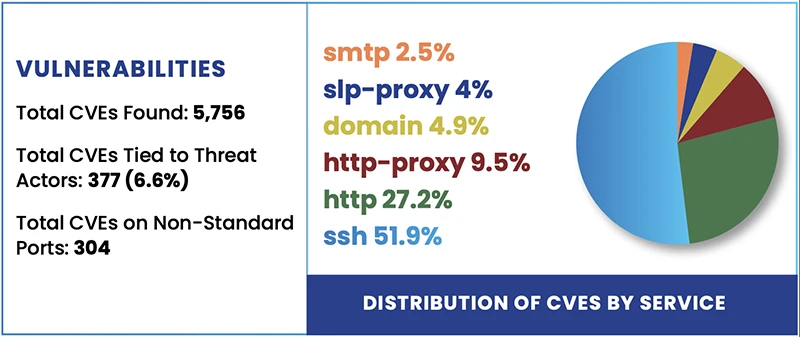
Many of America’s largest energy providers are exposed to known and exploitable vulnerabilities, and most security teams may not even…
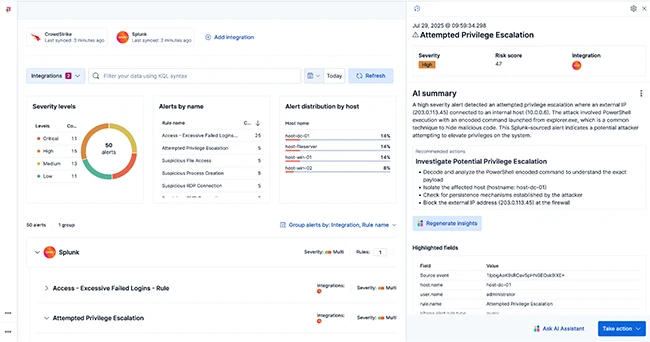
Elastic AI SOC Engine (EASE) is a new serverless, easy-to-deploy security package that brings AI-driven context-aware detection and triage into…
In this Help Net Security interview, Jordan Avnaim, CISO at Entrust, discusses how to communicate the quantum computing threat to…