Category: ITSecurityGuru
Leading global application security provider Black Duck has reinforced its commitment to the Saudi Arabian market with the introduction of…
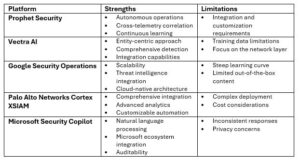
As threats evolve in sophistication and frequency while cyber skills gaps persist, Security Operations Centres (SOCs) are increasingly turning to…
Philadelphia-based cybersecurity firm HostBreach is offering a free CMMC Cyber Snapshot to businesses looking to maintain CMMC compliance. In particular, this refers…
Advanced Cyber Defence Systems (ACDS) has today unveiled plans for further global expansion with the establishment of its new French…
Keeper Security has unveiled an update to its password management platform: Keeper’s upgraded One-Time Share. The new feature enables bidirectional,…
With Infosecurity Europe around the corner next week, planning your schedule can be tricky. But never fear! The Gurus have…
Companies want results fast, and low/no-code (LCNC) and Vibe Coding platforms promise just that: rapid application development with either no…
Check Point Software has announced the launch of its next generation Quantum Smart-1 Management Appliances. These appliances deliver 2X increase…
Check Point has announced significant advancements to its Quantum Force Security Gateways family. As a result, all Quantum Force Security…
Check Point Software has announced a definitive agreement to acquire Veriti Cybersecurity, the first fully automated, multi-vendor pre-emptive threat exposure…
In today’s digital workplaces, more employees are building their own applications by generating code using Low Code No Code (LCNC),…
Cybersecurity researchers at Huntress have issued a warning after confirming active exploitation of a critical remote code execution (RCE) vulnerability…