Category: Mix
The Mines of More-Agree-Ah Once more I’m writing alone in my room at a Semgrep off-site, crackling fires and s’mores…
Security is built by people. At Intigriti, we don’t just help organizations stay secure; we shine a light on the ethical hackers making a difference. Through…
Security is built by people. At Intigriti, we don’t just help organizations stay secure; we shine a light on the ethical hackers making a difference. Through…
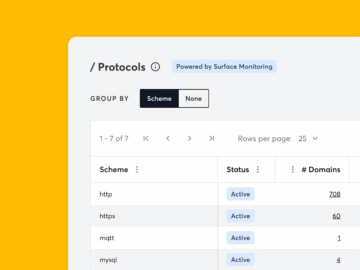
Most tools will just tell you that a port is open. We’ve decided that’s not enough. TLDR: We’ve launched Protocol…
I have a lot of thoughts on how AI will affect things, including bug bounty. And most of it is…
All the best influencers hate Anthropic right now, and for good reason. They ruined everything, and they’re worthy of every…
I have a new concept I’m using everywhere in my AI engineering called Bitter-Pilled Engineering (BPE). The idea comes from…
Welcome to the latest edition of Bug Bytes! In this month’s issue, we’ll be featuring: How a read-only Kubernetes permission turned into…
Three things you need to thrive in a world that keeps changing February 19, 2026 I just thought of a…
I’m a fan of Truffle and Eduard’s research, they’ve been featured a lot in tl;dr sec. This should be a…
Report writing is an integral part of bug bounty or any type of vulnerability assessment. In fact, sometimes, it can…
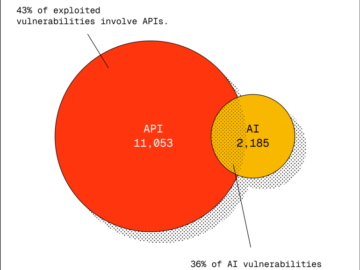
API security has been a growing concern for years. However, while it was always seen as important, it often came…
![[tl;dr sec] #317 – 100+ Kernel Bugs in 30 Days, Secret Scanning, Threat Actors Stealing Your PoC [tl;dr sec] #317 - 100+ Kernel Bugs in 30 Days, Secret Scanning, Threat Actors Stealing Your PoC](https://image.cybernoz.com/wp-content/uploads/2026/02/tldr-sec-317-100-Kernel-Bugs-in-30-Days-360x270.png)





![[tl;dr sec] #316 – How Trail of Bits uses Claude Code, GitHub Threat Intel, Open Source AI Pentesting Tools [tl;dr sec] #316 - How Trail of Bits uses Claude Code, GitHub Threat Intel, Open Source AI Pentesting Tools](https://image.cybernoz.com/wp-content/uploads/2026/02/tldr-sec-316-How-Trail-of-Bits-uses-Claude-360x270.png)