Category: Mix
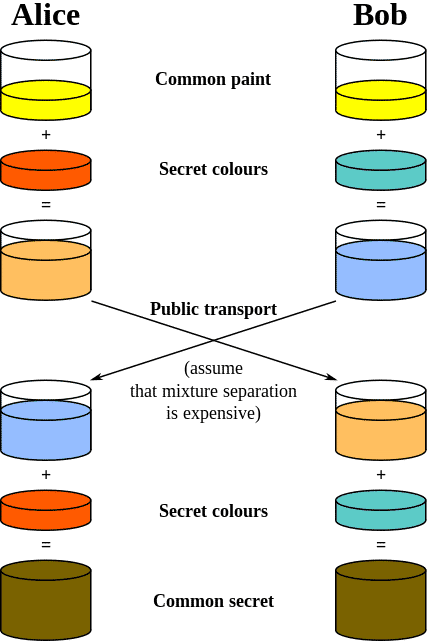
Diffie-Hellman is a key exchange protocol developed by Diffie and Hellman (imagine that) in 1976. The purpose of Diffie-Hellman is…
The time has come to dump Internet Explorer. I know, I know — you may have heard the same thing…
“Linux sucks as a desktop.” “Windows is insecure.” “OS X is for rich, trendy art majors.” Depending on who’s in…
[ Dec 31, 1999 ] Well, it is the day before. The day of, actually. As I write this it…
A new friend and I had an extraordinarily productive and meaningful discussion about religion last night. This is noteworthy because…
I’ve been studying web security again recently and decided to do a POC of CSRF (Sea Surf) (Cross Site Request…
I’ve been having a conversation with a friend about whether atheism and agnosticism is a belief. First off, let’s synchronize….
Anticipation of greatness is a near guarantee of mediocrity. It sucks to have to psyche yourself out, but it helps…
Nmap is the definitive port scanner. If you have any need for this sort of tool it would behoove you…
I will own a Rolex. Right now I am leaning toward the Submariner with the blue face. Color I am…
Why is it that nothing at all is of interest when you have 40 channels of T.V. in perfect clarity,…
When is it o.k. to draw humor from a subject or situation that is painful to others? Are there certain…