Category: Mix
Click and read the full-size version before continuing As someone who detests Trump, I think I finally figured out why…
SECURITY | AI | MEANING :: Unsupervised Learning is my continuous stream of original ideas, analysis, tooling, and mental models…
I think every creator might need to make a core decision of whether they’re doing: A PERSONAL brand on which…
SECURITY | AI | MEANING :: Unsupervised Learning is my continuous stream of original ideas, analysis, tooling, and mental models…
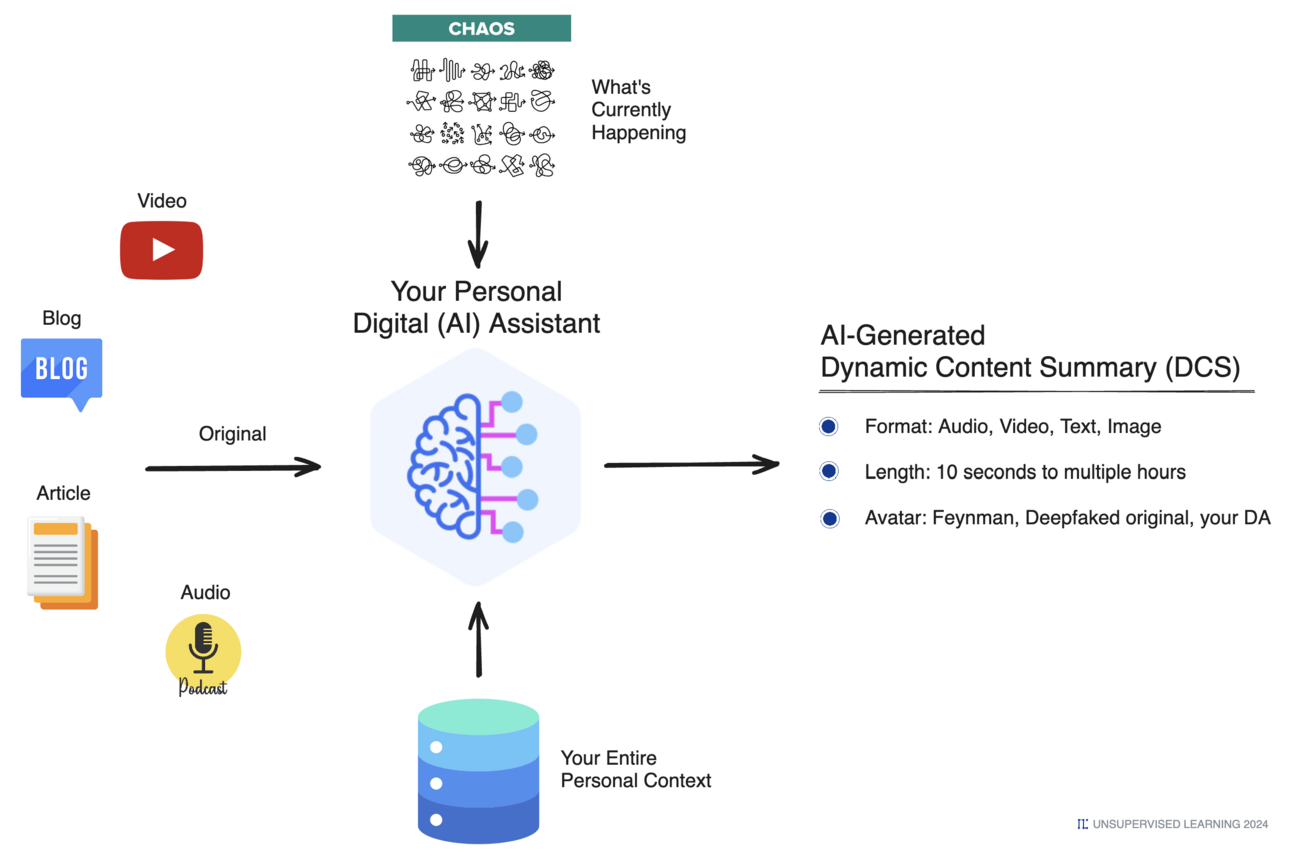
Click for Full Size Table of Contents I think a large percentage of media, including education, is about to be…
SECURITY | AI | MEANING :: Unsupervised Learning is my continuous stream of original ideas, story analysis, tooling, and mental…
I think a hidden tendency towards a belief in Libertarian free will is at the root of people’s opinion that…
SECURITY | AI | MEANING :: Unsupervised Learning is a stream of original ideas, story analysis, tooling, and mental models…
Table of Contents I have been thinking a lot about the competition between OpenAI, Anthropic, Meta, and Google for who…
On the 8th of October in 2027, an alien craft was seen entering the atmosphere over the Atlantic around 600…
Table of Contents A new way to explain LLM-based AI Thanks to Eliezer Yudkowsky, I just found my new favorite…
Table of Contents The feeling If you’re like me, you’ve had this strange, uneasy feeling about the job market1 for…