Category: Mix
SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
Jun 13, 2024 Resolving ZAP 2.15 Crashes on macOS with Java Version Issues Recently, I encountered persistent crashes while running…
I hope you’ve been doing well! Recently Overheard It’s late so you must forgive me for the brief intro. Some…
Started watching the second season of Severance. It’s. So. Good. And that soundtrack is such a classic. It reminds me…
SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
Oct 20, 2024 Using Deadfinder and GitHub Actions for Seamless Link Management A dead link, or broken link, occurs when…
Daniel Allen | 11 September 2024 at 06:53 UTC Performance is a critical factor in the usability and efficiency of…
Insights from Chinese intel reports on the NSA’s TTPs, understanding and testing passkeys, how Databricks leverages AI to focus on…
A while ago I asked what you wanted me to improve. This led to me revamping part of my premium…
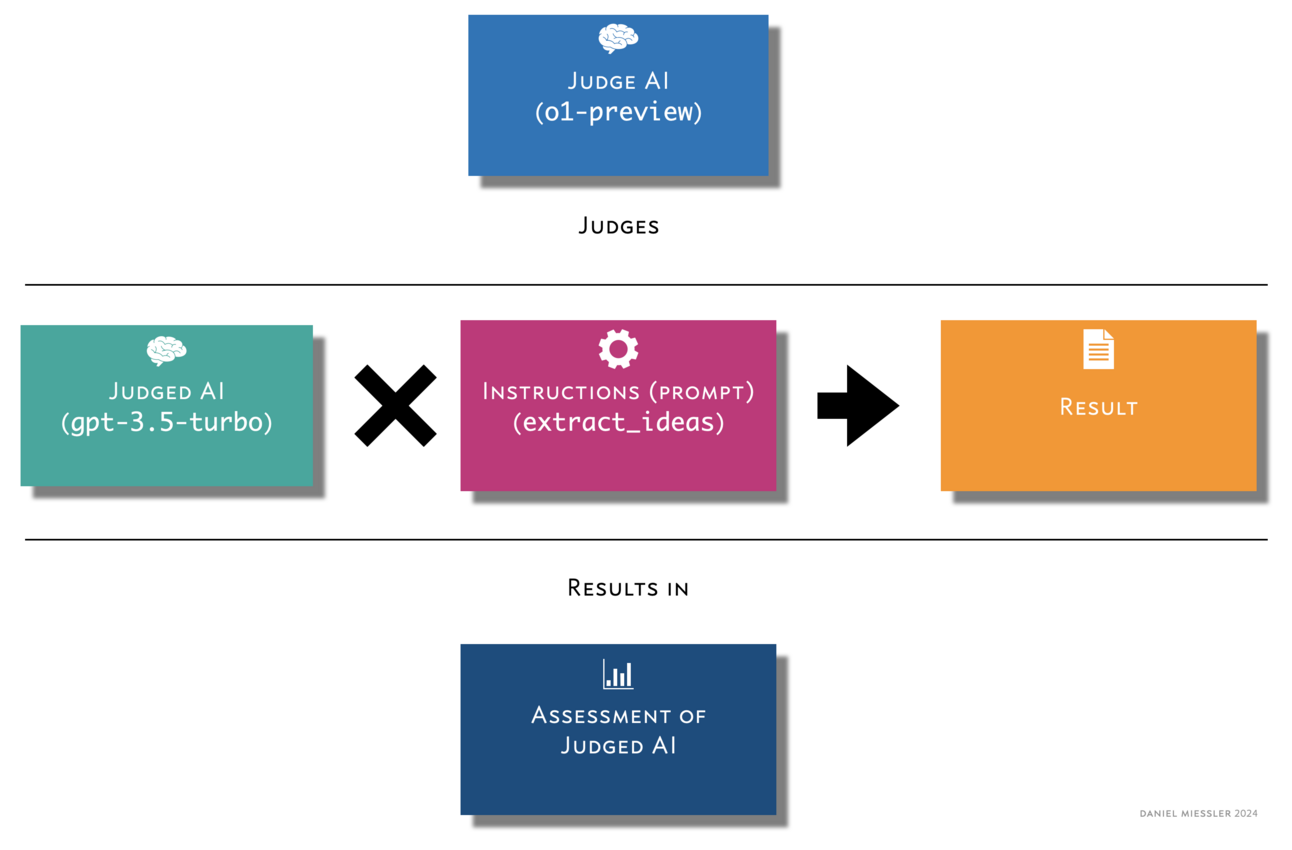
The structure of the rate_ai_result Stitch Since early 2023 I’ve wanted a system that can assess how well AI does…
Nov 03, 2024 Detecting Secrets with Noir – The PassiveScan Advantage Hello, security enthusiasts! Today, we’re diving into the exciting…
Amelia Coen | 12 September 2024 at 11:55 UTC Hands-on security testers need the best tools for the job. Tools…


![[tl;dr sec] #266 – AI CVE Analysis, Hijacking Abandoned S3 Buckets, Doing Less in AppSec [tl;dr sec] #266 - AI CVE Analysis, Hijacking Abandoned S3 Buckets, Doing Less in AppSec](https://image.cybernoz.com/wp-content/uploads/2025/03/tldr-sec-266-AI-CVE-Analysis-Hijacking-Abandoned-S3.png)




![[tl;dr sec] #267 – China on the NSA, Passkeys, Prioritizing CVEs with AI [tl;dr sec] #267 - China on the NSA, Passkeys, Prioritizing CVEs with AI](https://image.cybernoz.com/wp-content/uploads/2025/03/tldr-sec-267-China-on-the-NSA-Passkeys-Prioritizing.png)