Category: Mix
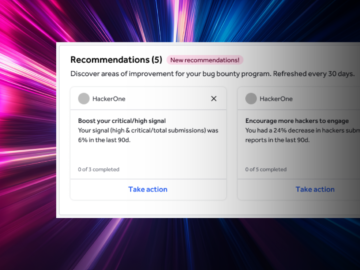
Meet HackerOne Recommendations: a built-in intelligence layer that continuously refines your security program, delivering personalized insights and your program’s historical performance….
When was the last time you checked DNS configurations for subdomains pointing at services not in use? According to Crowdsource…
There’s often a lack of understanding when it comes to DAST as a methodology versus DAST as a tool. How…
Talent Isn’t Your Savior, It’s Your Ceiling Talent is a high-risk gift. On the positive side, it gives you a…
Just when CIOs and CISOs thought they were getting a grip on API security, AI came along and shook things…
As I write this, the front page of GitHub.com declares in big bold letters that this is “Where the world…
Times and technologies change, but a few good ideas are still the same. With consistent application, a handful of wise…
It’s a comedy classic – you’ve got a grand idea. Maybe you want to build a beautiful new dining room…
How long does it take for a bug to get squashed, or for a pull request to be merged? What…
Coding up a to-do app may be the Hello, World of every framework, but when it comes to actually tracking…
Here’s a practice I use personally and encourage within my open source projects and any small teams I run for…
In order for chatbots and voice assistants to be helpful, they need to be able to take in and understand…