Category: Mix
I did a short post (and a video) about how AI shouldn’t be thought of as a bubble because a…
Andrzej Matykiewicz | 07 October 2025 at 13:17 UTC The latest Hacker-Powered Security Report from HackerOne makes one thing clear:…
Here’s an interesting frame I’m messing with. Maybe AI is disruptive to the labor market because it combines tools, operators,…
An honest reflection on the realities I’ve faced working as part of a Red Team I work as a security…
Qualys Pros Its unified platform provides a single pane of glass and powerful reporting capabilities that are ideal for satisfying…
I hope you’ve been doing well! Zero Signal Podcast – AI in Cybersecurity In Vegas this year I joined my…
For this Cybersecurity Awareness Month, we thought it important to draw attention to some of the most common and dangerous…
Andrzej Matykiewicz | 01 October 2025 at 14:31 UTC Bug bounty legend, NahamSec, has taken Burp AI for a spin….
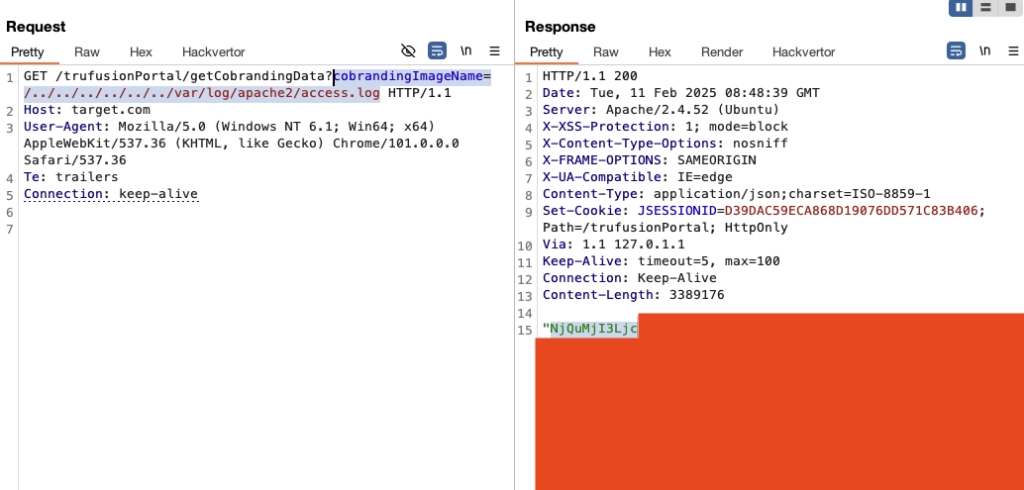
In early 2025, we encountered a mission-critical software component called TRUfusion Enterprise on the perimeter of one of our customers…
You asked, and we answered. At Intigriti, we’ve been paying close attention to the questions most frequently asked by those…
I keep hearing that world models are the way forward for AI. I tend to agree, and have been saying…
So here’s what I’ve been thinking about lately. We’ve got 8 billion people on this planet, right? And maybe—maybe—0.01% of…





![[tl;dr sec] #299 – The Security Engineer’s Guide to MCP, IAM Hound Dog, IMDS Anomaly Detection [tl;dr sec] #299 - The Security Engineer's Guide to MCP, IAM Hound Dog, IMDS Anomaly Detection](https://image.cybernoz.com/wp-content/uploads/2025/10/tldr-sec-299-The-Security-Engineers-Guide-to-MCP.png)