Category: Mix
Take Precision to the Next Level—Beyond Basic AI Efficiency and precision are critical in every operation. However, many security teams…
Learn more about bug bounty programs and how they work > The Growing Trend At HackerOne, we’ve observed a notable…
Efficiency and accuracy are crucial in vulnerability remediation. Yet, repetitive and manual handling of tasks throughout the vulnerability lifecycle remains…
The Challenge of Vulnerability Remediation When a vulnerability is identified, teams must determine the best approach to fixing it. This…
Addressing Inconsistencies in Vulnerability Scanning One of the primary challenges of vulnerability scanning is maintaining consistent results. Inconsistencies can lead…
NIS2 focuses on strengthening EU resilience through new and amended obligations for cybersecurity risk management practices, incident reporting, and security…
Pentesting has been around for decades, but it hasn’t undergone the revolution that other security practices have. Organizations tend to…
What Is Broken Access Control? BAC is a class of application vulnerability where a function or asset in the application…
According to the 7th Annual Hacker-Powered Security Report, IDOR makes up 7% of the vulnerabilities reported via the HackerOne platform. Government…
If you’re considering applying, here’s a look at what you can expect from the process, from the initial application to…
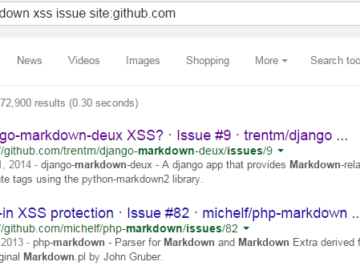
Exploiting Markdown Syntax Markdown is wonderful. In fact, this blog post itself is written in Markdown. I don’t need to…
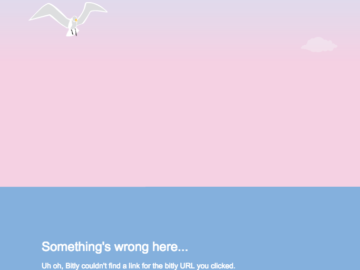
September 23 2015 · websec bruteforce As of late, a fair few companies and startups have been using dedicated URL…