Category: Mix
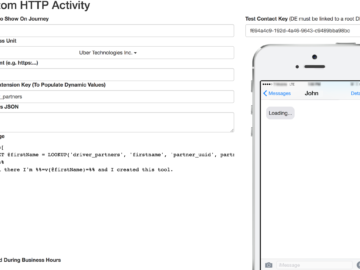
Effectively managing these risks requires human expertise and strategic oversight. That’s where the AI Risk Readiness Self-Assessment Tool comes in —…
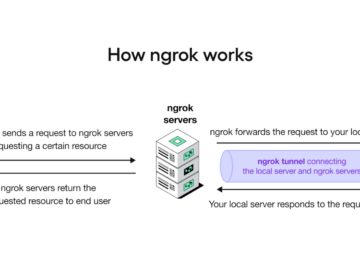
When gaining shell access to a machine on a network, a promising attack vector is to check the internal network…
Modern development and infrastructure management practices are fast paced and constantly evolving. In the race to innovate and expand, new…
The CRA will be a game-changing regulation for software and connected product security. The CRA imposes cybersecurity requirements for manufacturers…
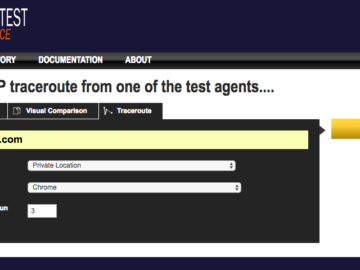
When Assetnote Continuous Security (CS) monitors your attack surface, one of the things it looks for are instances of WebPageTest….
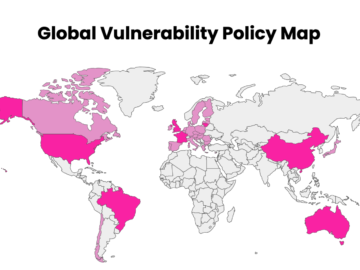
To help organizations keep up with the shifting landscape of VDP mandates and recommendations, HackerOne has developed the Global Vulnerability…
Motivations I recently made a video on how to find hidden files and folders on IIS through the use of…
The file upload vulnerability type is as broad in scope as the number of different file types. These vulnerabilities are…
What Is Cryptography? Cryptography is the practice and study of techniques for securing communication and information by transforming it into…
In fact, the Cloud Security Alliance’s Top Threats to Cloud Computing 2024 Report ranks the following concerns as the top three:…
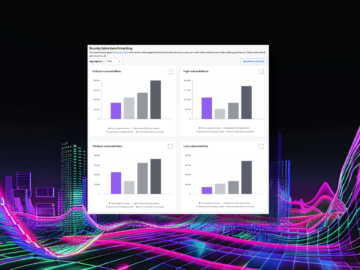
Without clear comparisons and long-term visibility, it’s challenging to identify areas for improvement and make informed, data-driven decisions. That’s why…
Security researchers and election technology manufacturers at the Election Security Research Forum (ESRF). The Event In preparation for the election…