Category: Mix
Many Facets, One Goal A common trope in cybersecurity is “don’t roll your own auth.” There’s a reason for this: implementing…
If you weren’t lucky enough to catch us at a roadshow event, you’ll be delighted to know you can catch…
This blog will break down the NIS2 Directive drawing information from the original directive briefing published by the European Parliament…
Retail and e-commerce organizations are major targets this time of year, which is why proactive security testing is essential to…
1. Are You Prepared to Manage Incoming Vulnerability Reports? Naturally, the purpose of running a bug bounty program is to…
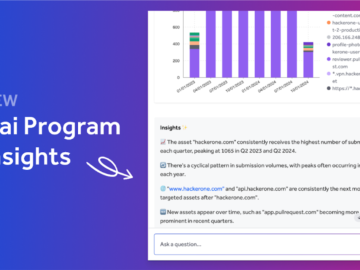
Transforming Security Program Management: A Day with Hai Picture this: It’s Monday morning, and your dashboard shows fifteen new vulnerability…
Employees at HackerOne utilize the Working Genius model, which provides individuals and teams with a straightforward, practical, and effective framework…
When Saskia joined the tech world, she didn’t follow the conventional path of computer science degrees or coding boot camps….
Earlier this year, the Office of Management and Budget (OMB), which establishes budget rules for federal agencies, issued a memorandum…
Q: Why did Deribit launch a bug bounty program? A: I like to view security as an onion where each…
Since then, we’ve grown the program, collaborated with HackerOne, and built partnerships within the bug bounty community. The valuable insights…
There are three factors that differentiate crypto and blockchain organizations from other industries; their attack surfaces, their most common vulnerabilities,…
![How an MFA Bypass Led to Account Takeover [Plus 11 Authentication Tips] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2025/01/How-an-MFA-Bypass-Led-to-Account-Takeover-Plus-11-360x270.png)


![Is Your Security Ready For Bug Bounty? [5 Questions] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2025/01/Is-Your-Security-Ready-For-Bug-Bounty-5-Questions-360x270.png)