Category: Mix
Since then, we’ve grown the program, collaborated with HackerOne, and built partnerships within the bug bounty community. The valuable insights…
Recent advances in AI technologies have granted organizations and individuals alike unprecedented productivity, efficiency, and operational benefits. AI is, without…
Earlier this year, the Office of Management and Budget (OMB), which establishes budget rules for federal agencies, issued a memorandum…
Employees at HackerOne utilize the Working Genius model, which provides individuals and teams with a straightforward, practical, and effective framework…
Before diving into security controls or implementing bug bounty programs, to first establish a strong foundation in risk management and…
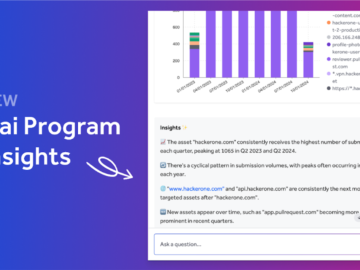
Transforming Security Program Management: A Day with Hai Picture this: It’s Monday morning, and your dashboard shows fifteen new vulnerability…
APIs have become the backbone of modern digital ecosystems, powering everything from mobile apps to e-commerce platforms. However, as APIs…
.bh__table, .bh__table_header, .bh__table_cell { border: 1px solid #C0C0C0; } .bh__table_cell { padding: 5px; background-color: #FFFFFF; } .bh__table_cell p { color:…
Authentication vulnerabilities are fun to find as they are impactful by nature and often grant unauthorized users access to various…
Cybersecurity is stretched thin. We all know it, so why state it again? Because cybersecurity is thinner today than yesterday….
The tech sector breathed a sigh of relief when the Federal Reserve confirmed its bail out of Silicon Valley Bank…
In my last blog, I examined why cybercrime increases during economic hardship and why innovation and vigilance are necessary to…