Category: Mix
Detecting Secrets with Noir – The PassiveScan Advantage Hello, security enthusiasts! Today, we’re diving into the exciting new features of…
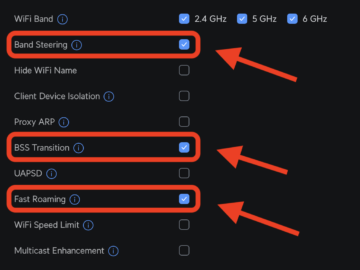
The three settings I had to enable to get proper WiFi roaming The problem I’m a massive fan of Ubiquiti…
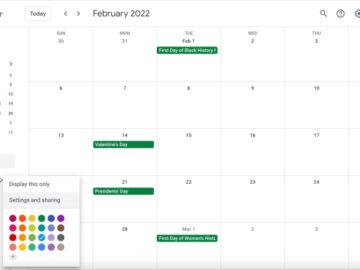
Today I learned that Google Calendar has a really useful CSV import feature that lets you bulk-import events. This is…
In this blog, we’ll explore who is and should be accountable for AI risk within organizations and how to empower…
Overview of the FortiManager API Vulnerability Recently, a critical API vulnerability in FortiManager (CVE-2024-47575) was disclosed. Certain threat actors exploited…
Rob Samuels | 30 October 2024 at 09:12 UTC Manage your security, your way. Managing a complex, enterprise-level web estate…
Security researchers and election technology manufacturers at the Election Security Research Forum (ESRF). The Event In preparation for the election…
Bug bounty hunters who spend time in content discovery and reconnaissance, in general, are always rewarded well for their efforts…
Without clear comparisons and long-term visibility, it’s challenging to identify areas for improvement and make informed, data-driven decisions. That’s why…
False positives in API security are a serious problem, often resulting in wasted results and time, missing real threats, alert…
For anyone struggling career or purpose-wise, I have a diagnostic for you. I believe one of the biggest problems in…
What Is Cryptography? Cryptography is the practice and study of techniques for securing communication and information by transforming it into…