Category: Mix
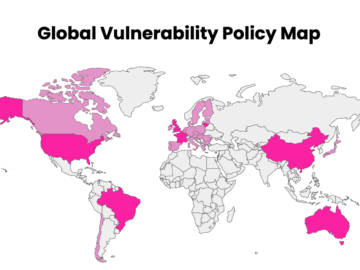
To help organizations keep up with the shifting landscape of VDP mandates and recommendations, HackerOne has developed the Global Vulnerability…
Earlier this year, we launched a new Domains page to give you more powerful and flexible attack surface insights. When…
Ollama is one of my favorite ways to experiment with local AI models. It’s a CLI that also runs an…
If you’re considering applying, here’s a look at what you can expect from the process, from the initial application to…
According to the 7th Annual Hacker-Powered Security Report, IDOR makes up 7% of the vulnerabilities reported via the HackerOne platform. Government…
You need an API security solution. That much is a given (although some may argue it isn’t!). While essential for…
When people look at the various projects I’ve put out over the last year, they often ask which is the…
Today, I’m going to share a quick automation trick that will save your eardrums and maybe even your sanity. The…
Cybersecurity is not just an IT concern, but a business imperative. Cyber threats pose significant financial, reputational, and legal risks….
Our users secure products and services developed by dozens of distributed technical teams. They rely on tools like Detectify to…
Andrej Karpathy recently tweeted this: “Input optional product Don’t ask your users for input. Coming up with input is hard,…
NIS2 focuses on strengthening EU resilience through new and amended obligations for cybersecurity risk management practices, incident reporting, and security…