Category: Mix
As a technical person who leads a technical team, I know firsthand that it can be easy to get lost…
It’s a comedy classic – you’ve got a grand idea. Maybe you want to build a beautiful new dining room…
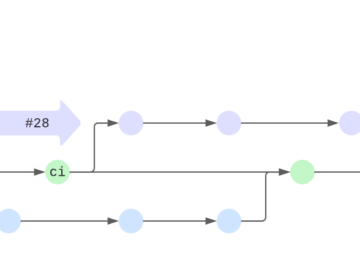
How long does it take for a bug to get squashed, or for a pull request to be merged? What…
In order for chatbots and voice assistants to be helpful, they need to be able to take in and understand…
1. Retail and E-commerce Are Prone to Credential-based Attacks “Credential-based attacks are evergreen.” When asked what significant security threats are…
Cross-site request forgery—or for short CSRF—vulnerabilities are one of the most exploited web security vulnerabilities that result in performing unwanted…
Amelia Coen | 23 August 2024 at 07:44 UTC The modern web is constantly developing, with new potential vulnerabilities emerging…
I’ve been thinking a lot about the whole “data wall” thing with LLMs lately. It’s the idea that LLMs can’t…
As I write this, the front page of GitHub.com declares in big bold letters that this is “Where the world…
Coding up a to-do app may be the Hello, World of every framework, but when it comes to actually tracking…
Here’s a practice I use personally and encourage within my open source projects and any small teams I run for…
I love websites. I love static sites in particular. But I know that sometimes it’s just not practical to write…