Category: Mix
Effective vulnerability management is no longer just an IT concern; it’s a fundamental business imperative that affects every layer of…
Our Solution: Precision Internal Network Testing with Zero Trust Control We are excited to introduce Gateway Internal Network Testing (INT) as the…
Tl;DR; An OAuth misconfiguration was discovered in the redirect_uri parameter at the target’s OAuth IDP at https://app.target.com/oauth/authorize, which allowed attackers…
Rob Samuels | 31 July 2024 at 12:17 UTC More comprehensive scans. More vulnerabilities identified. More time saved. Enhance your…
What Is an Authentication Bypass Vulnerability? An authentication bypass vulnerability is a weakness in a system that fails to protect…
Summary A significant vulnerability (CVE-2024-41110) was recently discovered in Docker Engine version 18.09.1.Although the issue was identified and fixed in…
@kinugawamasato가 정말 멋진 페이로드를 가지고 왔습니다. 최근 글 XSS Bypass: alert_?_(45)에서 이야기 드렸듯이 요즘 XSS 벡터에 대한 리서치가 활발해지고 있는데요,…
Our first-ever Recharge Week – July 1–5, 2024—aimed at giving most company employees a simultaneous week off to rest, pursue…
HIPAA regulatory standards outline the lawful use, disclosure, and safeguarding of protected health information (PHI). Any organization that collects or…
.bh__table, .bh__table_header, .bh__table_cell { border: 1px solid #C0C0C0; } .bh__table_cell { padding: 5px; background-color: #FFFFFF; } .bh__table_cell p { color:…
We talked to Naz Bozdemir, Product Marketing Lead, about her unique path and asked her to share insights into her…
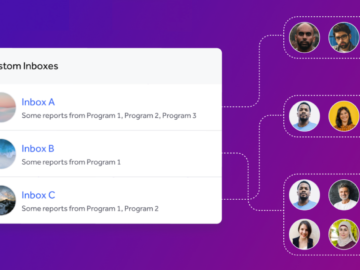
Introducing Custom Inboxes Custom Inboxes provide our enterprise customers with unparalleled flexibility in report management. Now, organizational administrators can create,…