Category: Mix
In our recent webinar, we delved into the concept of creating an API security playground tailored for both developer and…
In this blog post, I’m going to describe a relative new vector to achieve remote code execution via a JNDI…
We’re gearing up with some seriously cool stuff for Black Hat! But first, a little sneak peek – not just…
This year’s Hack Week was dedicated to artificial intelligence (AI), and teams worked together to problem-solve and explore new projects,…
The Problems Customers Use Ethical Hackers To Solve Organizations work with ethical hackers to address a range of issues, including…
Each year, we celebrate the GitHub Security Bug Bounty program, highlighting impressive bugs and researchers, rewards, live hacking events, and more….
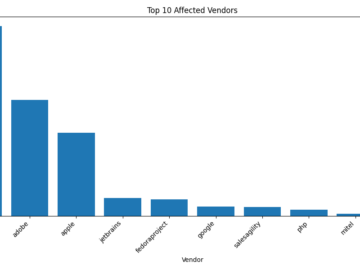
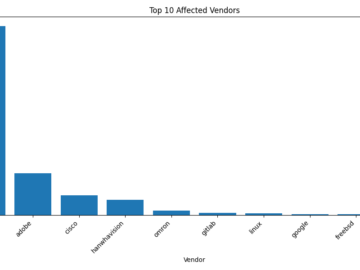
This Week’s Vulnerability Landscape Welcome to our weekly vulnerability trends report. This week, we’ve analyzed 2000 vulnerabilities to bring you…
This Week’s Vulnerability Landscape Welcome to our weekly vulnerability trends report. This week, we’ve analyzed 2000 vulnerabilities to bring you…
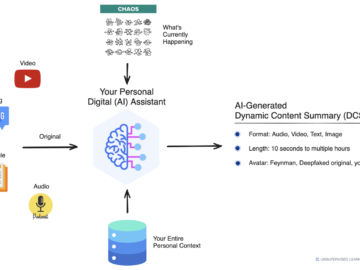
One of the coolest things I can’t wait to come out of AI is what I’m calling Dynamic Content Summaries…
When a potential threat emerges, organizations must act quickly. Yet despite this urgency, response times often lag, leaving systems vulnerable…
I think every creator might need to make a core decision of whether they’re doing: A PERSONAL brand on which…
Pentest reports are a requirement for many security compliance certifications (such as ISO 27001 and SOC 2), and having regular pentest reports…