Category: Mix
Did you know your MacBook has a built-in barista? Well, sort of. It’s called ‘caffeinate’, and it’s a nifty little…
The Talent Acquisition team currently has a net promoter score (NPS) of 56%, while the industry standard is 50%. However,…
Monzo is launching its public bug bounty program, a strategic step to bolster online security. With a keen focus on…
Polyfill.io helps web developers achieve cross-browser compatibility by automatically managing necessary polyfills. By adding a script tag to their HTML,…
Remediating Vulnerabilities Streamlining communication between hackers and security teams, HackerOne customers are able to quickly and thoroughly remediate vulnerabilities before…
DORA focuses on Information and Communications Technology (ICT) systems and applies to all financial institutions in the EU. This includes…
The role of ethical hackers in cybersecurity teams has become more crucial than ever. With the increasing complexity and frequency…
Most software companies resort to using third-party solutions for completing certain tasks within their company. A common example is a…
Labeled as CVE-2024-6387, the recently discovered vulnerability in OpenSSH has become a serious cause for concern among Linux servers. OpenSSH…
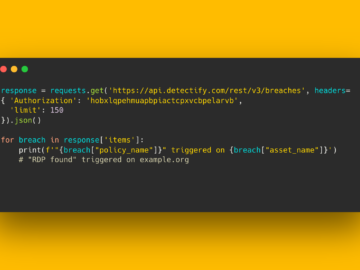
All Surface Monitoring users can configure Attack Surface Policies directly from the new Domains page, enabling various combinations of characteristics…
A security flaw that impacts specific versions of GitLab’s Community and Enterprise Edition products was just detected. This vulnerability can…
Click and read the full-size version before continuing As someone who detests Trump, I think I finally figured out why…