Category: Mix
I hope you’ve been doing well! 🎭️ SF SketchFest One of my favorite events every year is SF SketchFest, which…
Do you know what 23andMe, Jason’s Deli, North Face, and Hot Topic have in common? They’ve all been breached by…
Introduction On January 16 2024, Atlassian issued a significant alert on a critical Server-Side Template Injection (SSTI) vulnerability in Confluence…
Unsupervised Learning is a security, AI, and meaning-focused newsletter that looks at how best to thrive as humans in a…
In this episode of Unsupervised Learning, we talked to Shil Sircar. Shil is the Senior VP of Engineering and Data…
The Wallarm Security Research team is pleased to share the latest version of our API ThreatStats report. This report serves…
Premium Content This content is reserved for premium subscribers of Unsupervised Learning Membership. To Access this and other great posts,…
The participants answered live as well as carefully curated questions from popular community platforms such as Quora, Reddit, and LinkedIn….
I hope you’ve been doing well! 🐕️ Dogn’t You Dare Last week, I shared that recently I slid on something…
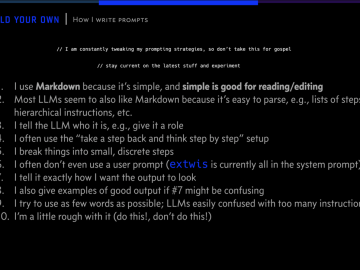
If you want AI to work for you, you have to know how to talk to it. I’ve been grinding…
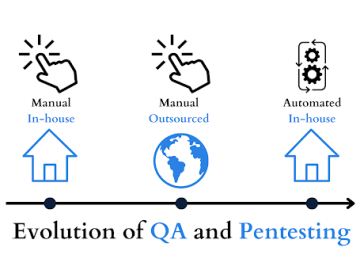
Quality assurance in software development is a process of ensuring that software, once it’s deployed to production, will be free…
Unsupervised Learning is a Security, AI, and Meaning-focused newsletter and podcast that looks at how best to thrive as humans….
![[tl;dr sec] #216 – Azure Attack Paths, Recipe for Scaling Security, Cybersecurity Incident Tracker [tl;dr sec] #216 - Azure Attack Paths, Recipe for Scaling Security, Cybersecurity Incident Tracker](https://cdn.cybernoz.com/wp-content/uploads/2024/02/tldr-sec-216-Azure-Attack-Paths-Recipe-for-Scaling-360x270.png)






![[tl;dr sec] #215 – Cloud Threat Landscape, Web LLM Security Labs, Azure Logs Primer [tl;dr sec] #215 - Cloud Threat Landscape, Web LLM Security Labs, Azure Logs Primer](https://cdn.cybernoz.com/wp-content/uploads/2024/01/tldr-sec-215-Cloud-Threat-Landscape-Web-LLM-Security-360x270.png)