Category: Mix
Table of Contents I have been thinking a lot about the competition between OpenAI, Anthropic, Meta, and Google for who…
On the 8th of October in 2027, an alien craft was seen entering the atmosphere over the Atlantic around 600…
Table of Contents A new way to explain LLM-based AI Thanks to Eliezer Yudkowsky, I just found my new favorite…
The feeling If you’re like me, you’ve had this strange, uneasy feeling about the job market for a few years…
SECURITY | AI | MEANING :: Unsupervised Learning is a stream of original ideas, story analysis, tooling, and mental models…
I think I finally figured out what art is. Took me decades. Here’s my definition, which has two primary components:…
I think InfoSec—and in fact business management in general—is evolving into the combination of four things: Policy (entity identity/goals) State…
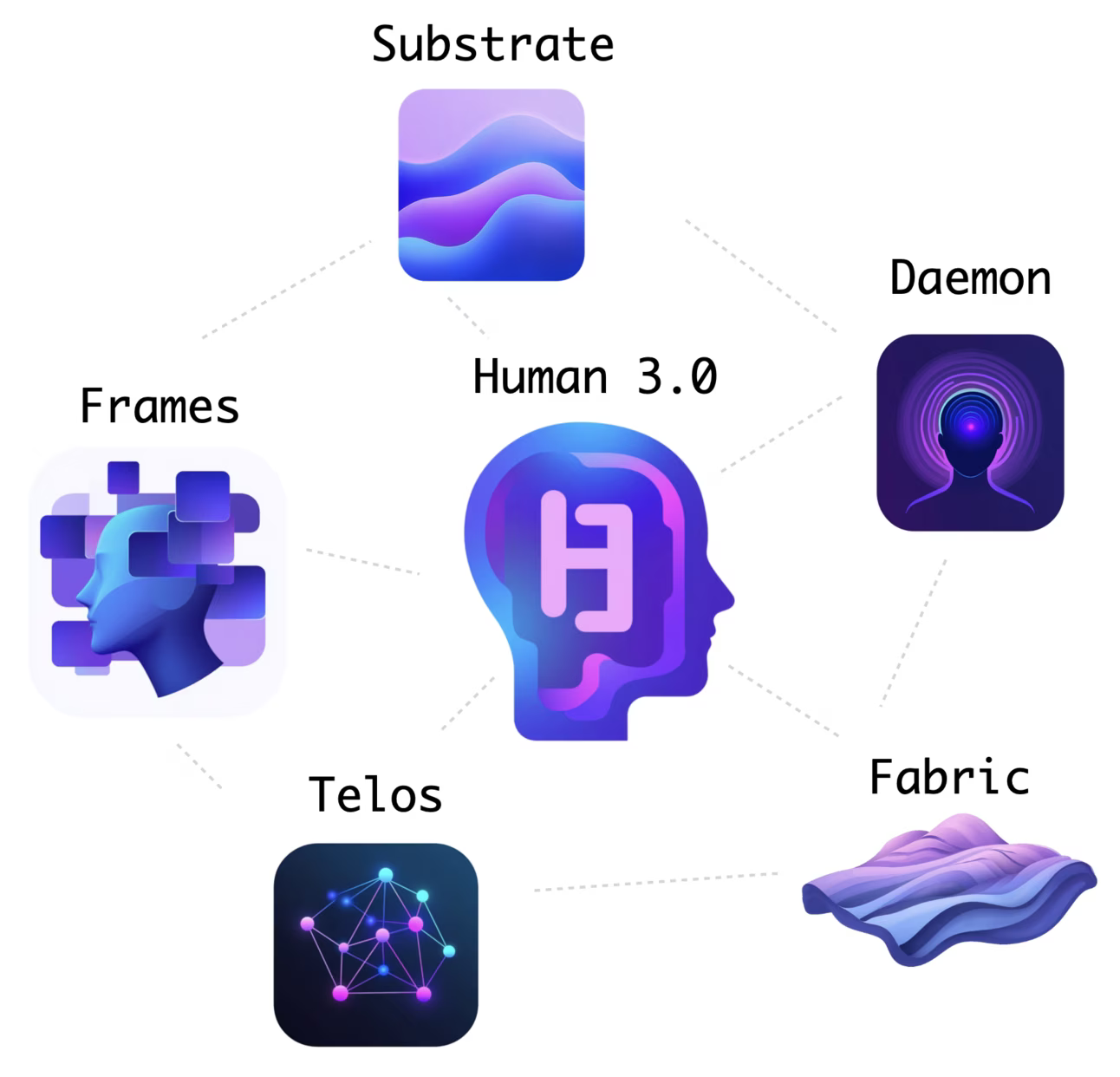
When people look at the various projects I’ve put out over the last year, they often ask which is the…
SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
Ollama > is one of my favorite ways to experiment with local AI models. It’s a CLI that also runs…
I think people are confused about how money will be won and lost with AI. Most “AI businesses” will get…
meaning from focus For anyone struggling career or purpose-wise, I have a diagnostic for you. Fill in this sentence. the…