Category: Mix
Automated scanners and tools are noisy; they do not know your business and can’t extrapolate context to truly understand validity…
Emma Stocks | 14 November 2023 at 08:27 UTC You’ve might have heard of Lambdas. But have you heard of…
Unsupervised Learning is a Security, AI, and Meaning-focused podcast that looks at how best to thrive as humans in a…
최근에 Firefox쪽에서 하나 업데이트를 예고 했습니다. 곧 img 태그에만 존재하던 lazy-loading이 iframe에도 적용되는데요. 성능적인 장점은 분명히 있겠지만, img와 달리 XSS의…
동시성 프로그래밍은 재미있지만 구조나 사이즈에 따라 어려움을 동반합니다. 개인적으로도 도구 작성 시 자주 사용하기 때문에 제가 진행하는 프로젝트에서 자주 볼…
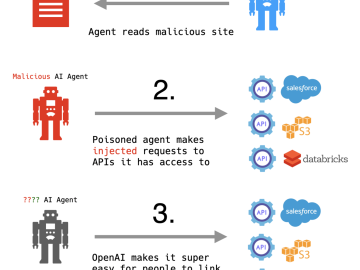
AI Agents + API Access + Prompt Injection So I want to talk real quick about the recent announcements from…
Pressing to active the Humane AI Pin I should be all about the new Humane AI pin. But I’m not,…
In early November, the cybersecurity community witnessed the exploitation of a zero-day vulnerability in Confluence Data Center and Server. This…
To ensure that AI is more secure and trustworthy, the EO calls on companies who develop AI and other companies…
People are thinking a lot about when we’re going to get AGI, and I think it’s coming faster than most….
What Is Pentesting? Pentesting attempts to ethically breach a system’s security for the purpose of vulnerability identification. In most cases,…
New and Upcoming Public Policy on VDPs VDPs are in the midst of a shift from an industry best practice…





![AI Red Teaming: HackerOne’s Approach [Playbook] Hackerone logo](https://cdn.cybernoz.com/wp-content/uploads/2023/11/AI-Red-Teaming-HackerOnes-Approach-Playbook-360x270.png)

![Bug Bounty Vs. Pentest [Differences Explained]unty vs. Penetration Testing: What’s the Difference? Hackerone logo](https://cdn.cybernoz.com/wp-content/uploads/2023/11/Bug-Bounty-Vs-Pentest-Differences-Explainedunty-vs-Penetration-Testing-Whats-360x270.png)