Category: Mix
Smart Pension, one of the fastest-growing financial technology companies in the UK, is launching its Vulnerability Disclosure Program (VDP). Ever…
Pick between Samantha from Her or TARS from Interstellar OpenAI just added super-high-quality voices to ChatGPT, and you can now…
HackerOne’s AI can already be used to: 1. Help automate vulnerability detection, using Nuclei, for example 2. Provide a summary…
Snippet When you hear “Application Layer Gateway,” or ALG for short, think of it as a network traffic conductor. It’s…
At HackerOne, we’ve always been committed to helping customers navigate the complex landscape of prioritizing vulnerability remediation. The CVE Discovery…
Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by…
I enjoy having my own list of quotations for two reasons: I hate not remembering my favorites. Favorite quotes serve…
Introduction It’s time for another round Citrix Patch Diffing! Earlier this month Citrix released a security bulletin which mentioned “unauthenticated…
Unsupervised Learning is a Security, AI, and Meaning-focused podcast that looks at how best to thrive as humans in a…
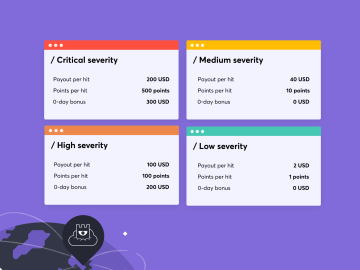
TL;DR: Starting November 1, 2023, the reward for each time a submitted module is found in customers’ assets (pay-per-hit) will…
You’re probably here because you just got a new HomeKey lock, or a new iPhone, or a new Apple Watch….
여러분들은 패스워드 매니저를 사용하시나요? 저는 개인적으로 Apple의 암호 기능을 주로 사용합니다. 또한 icloud+도 사용하고 있어 이메일 가리기 + 암호 조합으로…