Category: Mix
Note: this post currently just has content on AI + reverse engineering, but check back soon and I’ll be covering…
Izar describes the attributes required by threat modelling approaches in order to succeed in Agile dev environments, how to build…
Mukul Khullar, Staff Security Engineer, LinkedIn twitter, linkedinabstract slides video Mukul recommends a three step defense-in-depth process for mitigating these risks. 1….
An overview of functions-as-a-service (FaaS) and GraphQL, relevant security considerations and attacks, and a number of demos. What is Functions-as-a-Service…
Real TalkOne thing I appreciated about this talk is that Kelly and Nikki kept it real. Most blog posts, talks,…
An overview of the mobile and API security cat and mouse game (securely storing secrets, TLS, cert pinning, bypassing protections…
Vladimir de Turckheim, Software Engineer, Sqreen twitter, linkedinabstract slides video For vulnerabilities, a SQL injection example is given as well as regular…
The new Clear-Site-Data HTTP header allows a website to tell a user’s browser to clear various browsing data (cookies, storage,…
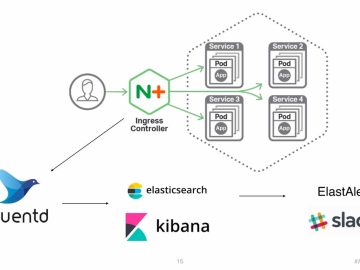
Stepan Ilyin, Co-founder, Wallarm twitter, linkedinabstract slides video How NGINX modules and other tools can be combined to give you a nice…
If you don’t get the process right, the technical stuff goes to waste. Background The Salesforce AppExchange was launched in…
In this talk, Tony discusses the economic and geopolitical impacts of supply chain attacks, a walkthrough of supply chain threat…
Elevation of Privilege: Background Adam originally created Elevation of Privilege at Microsoft as a fun and low barrier to entry…