Category: Mix
Below, the Detectify team has listed some of the largest security news and breaches of the past year, that have…
GitHub celebrated the fourth anniversary of its Security Bug Bounty program and released a comprehensive recap of a record-breaking 2017…
Cross-site scripting (XSS) is a type of attack that can be carried out to compromise users of a website. The…
The more the world gets hacked, the more we need hackers. We need white hats. They will find vulnerabilities so…
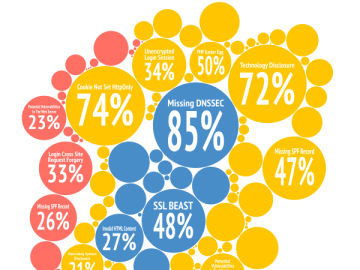
What do typical websites look like through the eyes of our vulnerability scanner the first time they are tested? How does…
Just over two years ago, General Motors became the first major automaker to launch a public vulnerability disclosure program (VDP)….
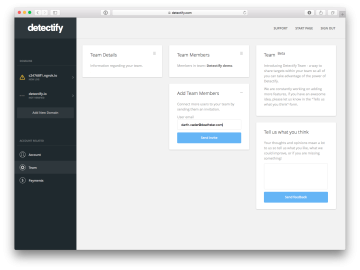
Security is not a one-man show. That’s why you can now add new users to your Detectify account and share…
“I am by trade now a CISO. So I have to care about risk and compliance all the time, which…
2015 ended on a high note for Detectify! Internetworld published their annual list of Sweden’s most exciting startups and we’re…
We are thrilled to introduce the newest member of the HackerOne team, Kathryn Haun, who is joining our board of directors….
The latest integration from Detectify is an integration with the incident manager system PagerDuty. Unlike the earlier integrations with Slack…
Shopify’s commerce platform has awarded hackers more than $850,000 in bounties for helping secure its $55 billion-plus customer transactions and…






![[Integration] You can now integrate Detectify with PagerDuty [Integration] You can now integrate Detectify with PagerDuty](https://cdn.cybernoz.com/wp-content/uploads/2023/05/Integration-You-can-now-integrate-Detectify-with-PagerDuty-304x270.png)
