Category: Mix
WordPress is amazing, we can’t argue with that. It’s efficient, powerful, and functional. However, given that it is the most…
As GDPR’s implementation date nears, more and more organizations are working to put in place the necessary pieces of their…
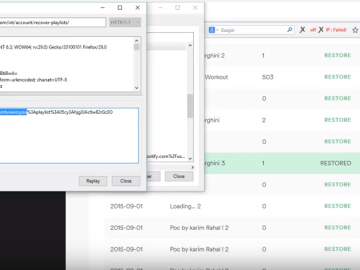
This video demonstrates a cross site request forgery web vulnerability and a privilege escalation vulnerability in the official Spotify online…
Cherry blossoms, melting snow, sunshine and a whole lot of hacking.Twenty-seven hackers representing nine countries gathered at the U.S. capital…
Once your business goes live online, you’re vulnerable to mayhem. Detectify’s CEO Rickard Carlsson explains why web security matters and…
It was 70 degrees, sunny and a Saturday, but everyone was inside. Forty-one hackers representing 11 countries. More than $400,000…
Have you ever wondered how we manage to test your website for hundreds of vulnerabilities without making you wait too…
Harri Hursti is one of the most knowledgeable hackers of election technology. He’s most known for the eponymous hack in…
The internet is awesome, but it can also be a pretty dangerous place. This is why we at Detectify are…
If you’re a new hacker on HackerOne, starting from scratch can appear daunting. Perhaps you’ve looked at the long list…
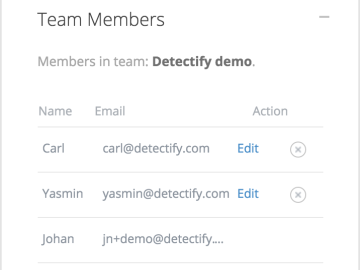
Detectify introduces permissions rights to Detectify teams. As a team administrator, you are now able to grant users two different…
GDPR compliance is so relevant today because, well, it comes into effect starting tomorrow, May 25, 2018. The time for…