Category: Mix
Ever wished there was an easy way to see if your site is vulnerable to any of the vulnerability categories…
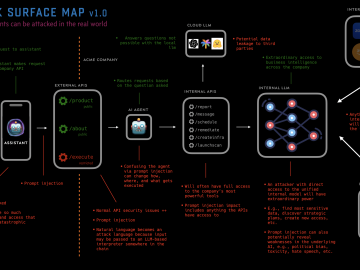
This resource is a first thrust at a framework for thinking about how to attack AI systems. At the time…
The next time your friend of colleague goes on about their fantasy league, remember it’s more than just a game….
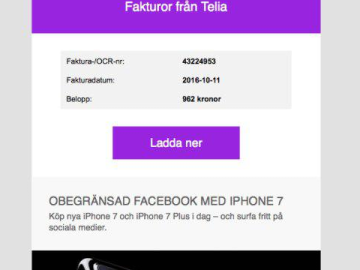
A phishing email that supposedly comes from Telia, a mobile network operator, has recently been doing the rounds in Sweden….
Johan Norrman is a proper IT veteran. He has always found companies in the early stages of development exciting, so…
“Give a (wo)man a fish and you feed them for a day;teach a (wo)man how to fish and you feed…
Security Awards is a yearly event arranged by the Swedish publication Skydd och Säkerhet, where the aim is to highlight…
This blog was written by GitHub’s Engineering Team and originally published here. GitHub launched our Security Bug Bounty program in 2014,…
As soon as WordPress launch a new version they publish a changelog on their website where you can find what…
What’s your favorite T-shirt? Maybe one from that conference you went to 5 years ago, a sleek threadless tee, or…
Many are most likely already familiar with CDNs, Content Delivery Networks, but in short, a CDN is a service where…
Continuous improvement is at our heart, and the Hacker Dashboard is an excellent example of how we’ve been iterating based…
![[Release] Check if your website passes the OWASP Top 10 test! [Release] Check if your website passes the OWASP Top 10 test!](https://cdn.cybernoz.com/wp-content/uploads/2023/05/Release-Check-if-your-website-passes-the-OWASP-Top-10-360x270.png)