Category: Mix
Each blog in the series “Breaking Down the Benefits of Hacker-Powered Pentests” has focused on one of the key findings…
Findings are a key component of our service, which is why we decided the finding details view deserved a facelift….
Hey there, I hope you’ve been doing well! Life Advice from VCs This week I found myself at a dinner…
Fueled by tremendous demand for hacker-powered security in the region, security veteran Attley Ng has joined HackerOne as Vice President…
To bring you the most up-to-date security service and help you stay on top of threats, we update Detectify on…
Phil Venables, senior advisor and board director at Goldman Sachs, has seen more than his share of highs and lows…
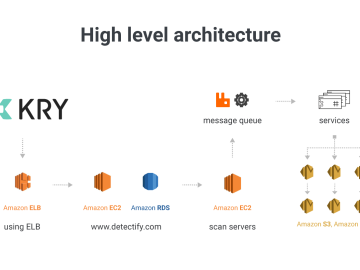
About the company: KRY offers video consultations with licensed doctors through their app and is revolutionizing the healthcare sector by…
Phil Venables, senior advisor and board director at Goldman Sachs, has seen more than his share of highs and lows…
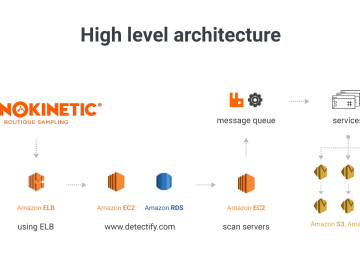
About the company Sonokinetic BV is a virtual instruments manufacturer based in the Netherlands catering to composers in the media…
Two years ago, Laurie Mercer joined HackerOne as a security engineer. Before that, he was a developer, penetration tester, and…
Security testing has historically been driven by annual compliance audits, but the rapid changes in web security require a new…
Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by…

![[tl;dr sec] #181 – Awesome CloudSec Labs, Red Team Infra in 2023, Privilege Escalation in EKS [tl;dr sec] #181 - Awesome CloudSec Labs, Red Team Infra in 2023, Privilege Escalation in EKS](https://cdn.cybernoz.com/wp-content/uploads/2023/05/tldr-sec-181-Awesome-CloudSec-Labs-Red-Team-Infra-360x270.jpg)