Category: Mix
In part 1 of web security trends 2020, we discussed the rise of Crowdsourced Security and the ever-changing attack surface….
The CISO of Flo Health, the world’s most popular women’s health app, knows that enabling his security team with the…
In 2020, both big and small companies alike are embracing pen-testing as a solution to ensure the quality and availability…
Q: Tell us who you are. I’m Robert Lowery, Senior Analyst at Hyatt. I’m part of the Vulnerability Management team,…
Some know him by his hacker handle, TomNomNom. UK-native Tom Hudson started at Detectify as a Senior Security Researcher, and…
Who is DC3’s DCISE? Krystal Covey: The Defense Collaborative Information Sharing Environment (DCISE) is the operational hub for the DOD’s…
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings,…
How Can You Use the Integration? This new integration reduces the manual processes of comparing and taking action on vulnerability…
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings, features and…
What is your role as an ambassador? 🌎 As an ambassador, I aim to foster a bug bounty community in…
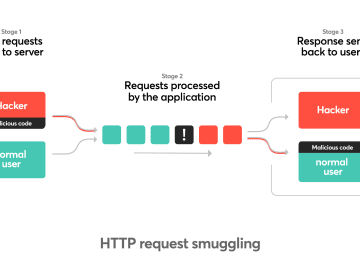
HTTP request smuggling is increasingly exploited by hackers in the wild and in bug bounty programs. This post will explain…
Today HackerOne announced new capabilities for AWS customers looking to improve security in their cloud applications. These include vulnerability pentests…