Category: Mix
Among the topics they explored included the success of their long-running bug bounty programs in discovering security vulnerabilities, how to…
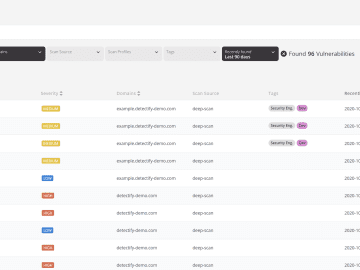
Triage is just as important to security teams as it is to hospital workers. Now, you can prioritize and remediate…
Midjourney is like using a Mac, and DALL-E is like using the Linux command line Created/Updated: August 21, 2022 Created…
Organizations need to identify, prioritize, and remediate these vulnerabilities as soon as possible. CVSS is a free and open industry…
Coming hot off our successful funding round of €21.5 million in November 2019, we had no plans of stopping –…
Created/Updated: September 7, 2022 In today’s standalone episode I’m going to talk about some new gaming ideas I’ve not seen…
December 17th Update: Vulnerabilities in Log4j have been evolving over the course of this week since the original disclosure of…
On November 6th, 2019, Detectify added security tests for 50+ of the most popular WordPress plugins, including Easy-WP-SMTP. Although the…
Created/Updated: September 21, 2022 My mom died on Saturday. My biological mother became unable to function when I was around…
Common Weakness Enumeration (CWE) is a system to categorize software and hardware security flaws—implementation defects that can lead to vulnerabilities….
Our Crowdsource ethical hacker community has been busy sending us security updates, including 0-day research. For Asset Monitoring, we now push out tests more…
Created/Updated: September 25, 2022 I’ve just started using Safari again after being on Chrome for a while, and one of…