Category: Mix
Created/Updated: January 23, 2023 Sam Altman, the CEO of OpenAI, has said multiple times that, He says it in this…
Why sensitive data controls need to be established long before you think you need them, as demonstrated by Google dorking. Last…
Are you a veteran hacker, someone who loves code review, or looking to get your first CVE? Then, I have…
STOCKHOLM, January 27, 2022. Detectify, the SaaS security company powered by ethical hackers, closed 2021 with significant corporate momentum propelled by…
Creativity is something you let out, not let in Created/Updated: January 31, 2023 This is member content. Thank you for…
An overview of how proxy servers form the basis of online anonymity, and how their use in various forms helps…
I recently participated as a panelist on a HackerOne press panel where there was a lot of discussion about AI…
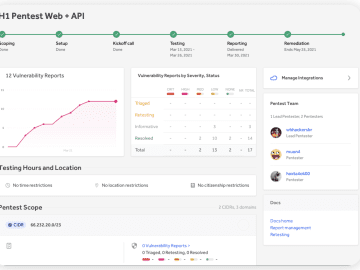
New capabilities improve pentesting to increase attack resistance The enhanced features drive robust security testing practices with the ability to…
Detectify is aiming to make security understandable and easy to work with. That is why we visualize your security status…
Exploring the intersection of security, technology, and society—and what might be coming next… Standard Web Edition | January 23, 2023…
A practical guide to moving to cloud services with minimal downtime, using AWS examples. For an application that’s ready to…
On July 4th, 2022, Chief Digital and Artificial Intelligence Office (CDAO), Directorate for Digital Services (DDS), DoD Cyber Crime Center…