Category: Mix
Wanna hack zseano website and get paid? – Bounty Thursdays #28 Source link
While researching a bug bounty target, I came across a web application that processed a custom file type. Let’s call…
In my last series, I discussed various ways of getting command execution in Windows environments when you’ve compromised a valid…
Guide to Entry Level Infosec Jobs Source link
URL validation bypass | Filedescriptor solves Intigriti’s XSS challenge Source link
While my last finding affecting SecurePoint’s UTM was quite interesting already, I was hit by a really hard OpenSSL Heartbleed…
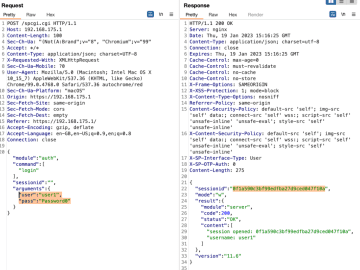
Broken Access Control – Lab #4 User role can be modified in user profile | Short Version Source link
XML External Entities (XXE) Explained Source link
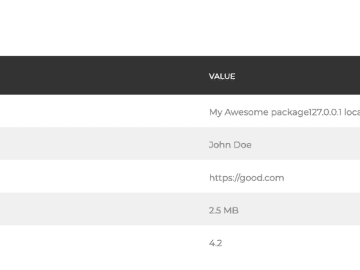
Matt Atkinson | 05 July 2022 at 08:39 UTC If you use Burp Suite Professional or Burp Suite Community Edition…
Cloud Hacking: Common Attacks & Vulnerabilities Source link
Can AI Create a Minecraft Hack? Source link
On May 7 it was World Password Day. A day on which a lot of awareness about password security is…