Category: Mix
10 Tips For Crushing Bug Bounties in the First 12 Months Source link
ZAP의 Site tree는 Burp와는 다르게 404 Not found도 보여주고 있습니다. 종종 쓸만한 정보가 되기 하지만 대체로 보기 불편한 존재입니다. ZAP에서는…
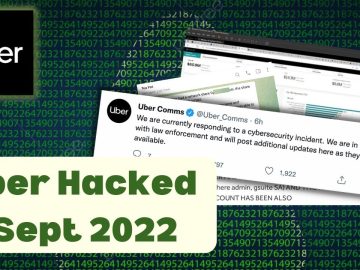
Uber Hacked – Sept 2022 | All Internal Dashboard | Slack Disabled #hack #uber #socialengineering Source link
HackerOne Live Hacking Event Recap: Las Vegas 2022 (H1-702) Source link
With this two-part blog series, we will delve into strategies and tactics exhibited by dozens of enterprise customers over several…
BSides Ahmedabad vlog!!! @BSidesAhmedabad Source link
Preliminary Enter exhibit one: An experienced engineer working for one of the biggest corporations in the world. This engineer had…
We shipped a new feature called Groups which allows users to organize assets, such as domains, according to any logic…
TECHNOLOGY NEWS Microsoft Taskmatrix.AIMicrosoft has introduced an AI API infrastructure called TaskMatrix.AI. It works by, “integrating foundation models with millions…
Commonly Misunderstood Bugs: DDoS & DOS Source link
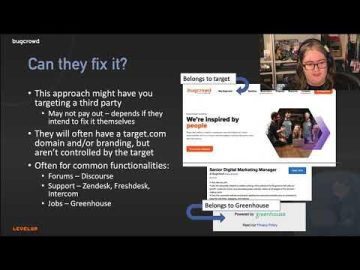
LevelUpX – Series 9: 8 Ways to (Almost) Never Get a Dupe Again with InsiderPhD (Katie Paxton-Fear) Source link
How much money I made in my 1st year of bug bounty? Bounty vlog #4 Source link