Category: Mix
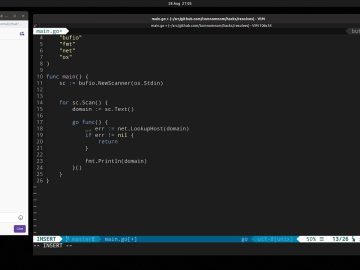
Basic concurrency in Go (Twitch Stream) Source link
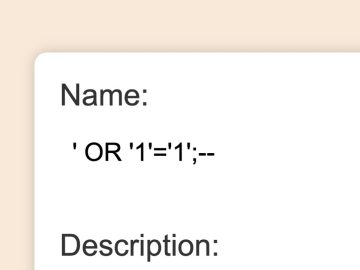
The Web Exploit That Would Make Harry Potter Jealous Source link
Elastic disclosed a bug submitted by dee-see: https://hackerone.com/reports/1636382 – Bounty: $4895 Source link
500K Subscriber Celebration! Source link
What makes Mastodon different from Twitter Source link
I opened on a malicious email attachment.. and this is what happened! Source link
One common perception is that it is easier to write rules for Semgrep than CodeQL. Having worked extensively with both…
Every pentester knows that amazing feeling when they catch a reverse shell with netcat and see that oh-so-satisfying verbose netcat…
On Apr 5, I had a look on Flickr login flow with Yahoo. Not after long I ran into a Flickr…
No BS Guide – Supercharge your Scripts with Xargs Source link
Applying root cause analysis to decision making Do you ever find your brain “connecting the dots” between multiple ideas or…
Hacking 1Password | Episode 2 – Decrypting the Protocol Source link