Category: Mix
We’re pleased to present the latest quarterly review and analysis of API vulnerabilities and exploits. This time, we’re going to…
Building a secure application in five steps | Security Simplified Source link
TomNomNom makes a digital VU meter with HTML canvas Source link
Hey there, I hope you’ve been doing well! Coffee Snobs Aficionados I’m not a big coffee person, but it seems…
I AM GIVING AWAY A CHROMEBOOK – 100k Twitter GiveAway Source link
8×8 disclosed a bug submitted by shriyanss: https://hackerone.com/reports/1825472 Source link
Solving the Pickle Rick CTF Source link
How to disable data persistence on Ubuntu using overlayroot Source link
Hi there! What a year it’s been right?! Let’s not mention the C word… it’s lockdown in 2hours here in…
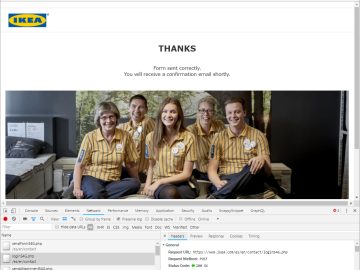
Proof of concept BackgroundPreviously we discussed a Local File Inclusion bug at IKEA.com, the bug was quite complicated and showed…
Three weeks ago I saw a blog post by fellow bug hunter, Jack Cable. The post both inspired and challenged…
Q: HOW do you find hidden stuff on websites? (this episode is all about CONTENT DISCOVERY!) Source link

![[tl;dr sec] #169 – Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS [tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS](https://cdn.cybernoz.com/wp-content/uploads/2023/03/tldr-sec-169-Top-10-Web-Hacking-Techniques-of-360x270.jpg)