Category: Mix
In 2016, my friend Daniel Miessler wrote a book called “The Real Internet of Things.” It’s a quick little read…
pnpm install -g ccusage I have a friend named Marcus Hutchins who doesn’t believe modern AI is intelligent. He thinks…
More powerful XSS scanning, Integration Dalfox v2.12.0 has been released. It’s been about three months since the previous version, 2.11,…
I think, looking back, we might say that the first week of July 2025 was the start of AGI. Like,…
Table of Contents The feeling If you’re like me, you’ve had this strange, uneasy feeling about the job market1 for…
I think we’re all in microcults now. Fractal microcults. Infinitely small ones. Cults of one. Not everyone, of course, but…
Rules files to vibe securely, earning $25K from dangling commits, compromising the extension marketplace of Cursor, Windsurf, and other VS…
The US government has taken another significant step towards strengthening cloud security with the release of CISA’s Binding Operational Directive…
There’s a popular idea going around right now about renaming “prompt engineering” to “context engineering.” The argument is that context…
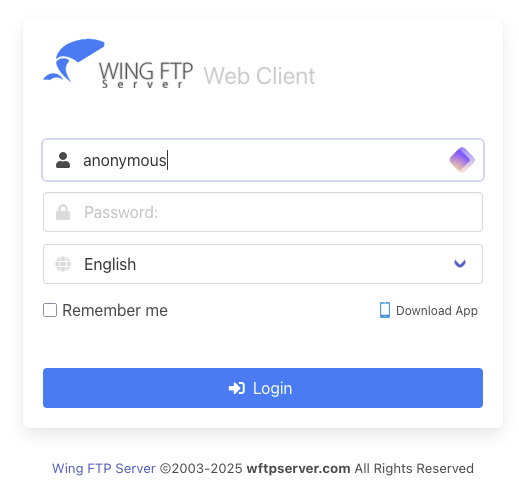
While performing a penetration test for one of our Continuous Penetration Testing customers, we’ve found a Wing FTP server instance…
Can LLMs red team AI, intro to detection engineering, how to scale security impact via cross-team partnerships I hope you’ve…
AI has had dramatic impacts on almost every facet of every industry. API security is no exception. Up until recently,…





![[tl;dr sec] #286 – Securing Vibe Coding, Finding Secrets “Oops Commits”, Backdooring IDE Extensions [tl;dr sec] #286 - Securing Vibe Coding, Finding Secrets "Oops Commits", Backdooring IDE Extensions](https://cdn.cybernoz.com/wp-content/uploads/2025/07/tldr-sec-286-Securing-Vibe-Coding-Finding-Secrets-Oops.png)
![[tl;dr sec] #285 – AI Red Teaming, Detection Engineering Field Manual, Building AppSec Partnerships [tl;dr sec] #285 - AI Red Teaming, Detection Engineering Field Manual, Building AppSec Partnerships](https://cdn.cybernoz.com/wp-content/uploads/2025/06/tldr-sec-285-AI-Red-Teaming-Detection-Engineering-Field.png)
