Category: Mix
People tend to love Starbucks despite their coffee tasting like it was brewed for three weeks in the center of…
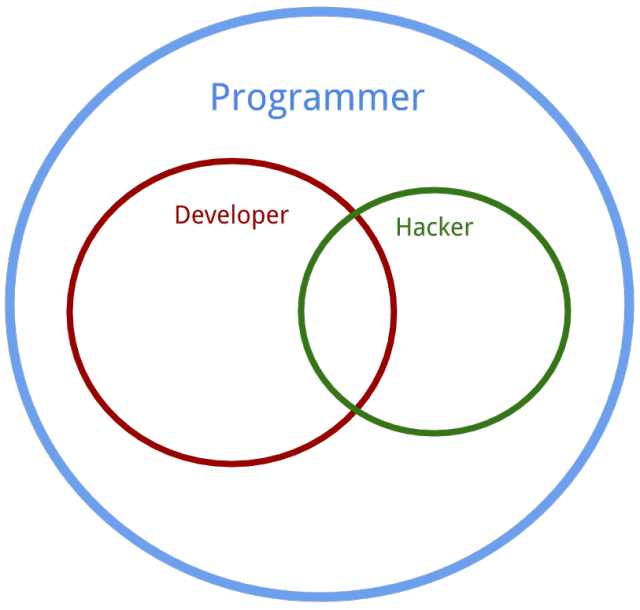
There is often spirited discussion and debate about the differences between Programmers, Hackers, and Developers. Most descriptions I’ve seen are…
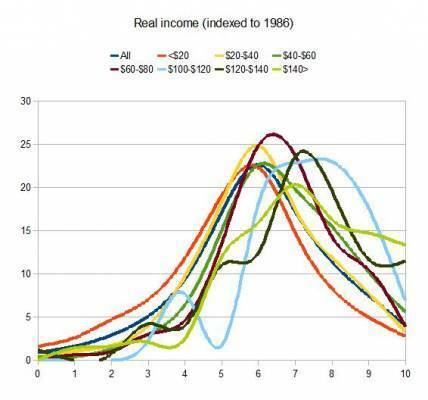
[ The graph’s x-axis shows the GSS WORDSUM score, which is a vocabulary-based intelligence proxy (correlated at .71). The y-axis…
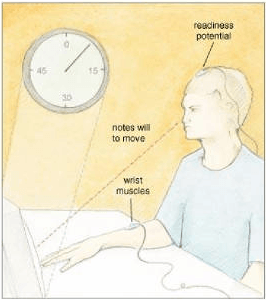
Image from skeptically.org In my ongoing efforts to convince others that free will is an illusion, I have found an…
For those not aware, Hacker Dojos are local groups found in high-tech areas that get many people together and have…
I wrote a few years ago about the only way I knew of to become immortal. Basically, it was the…
Image by pshan427 In both health and information security it’s easy to become conceptually constrained by external advice, recommendations, and…
I feel like I cannot be the only one who is disgusted every time I walk through someones exhaled cigarette…
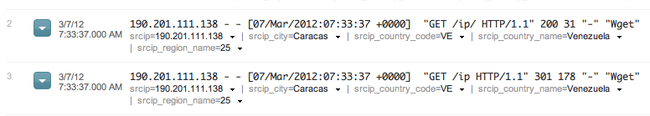
March 6, 2012 CloudFlare is a great service that proxies your site’s traffic in order to offer performance gains and…
Sam Harris’s book on free will came out today and I read it during dinner (it’s a short read). Here’s…
Before going into my qualms with Daniel Dennett’s capability/evitibility-based free will, I want to point out that most supporters of…
When open allocation is in play, projects compete for engineers, and the result is better projects. When closed allocation is…