Category: Mix
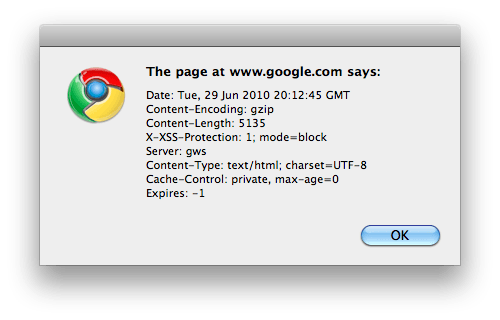
I was looking for a Google Chrome extension that did something like Firefox’s Live HTTP Headers recently and tripped over…
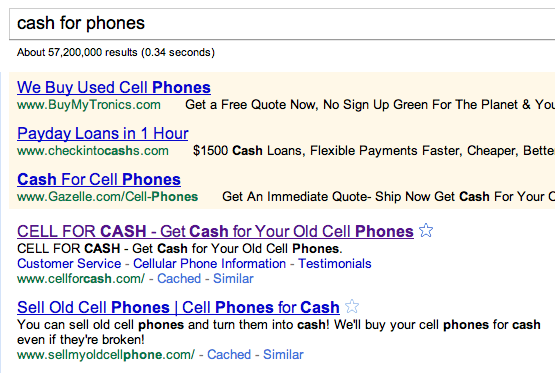
It’s pretty well accepted that one way to gauge something’s value is to see how it retains said value. One…
Flattr is an exciting new social networking / micro-payment service that allows you to set a donation amount that gets…
If you’re reading this you’re probably a bit geeky (like me), and you’ve no doubt been in at least 42…
Vibe coding is the latest trend sweeping through developer communities. It’s the art of describing a concept, feeding it to…
I’m reading a Bertrand Russell book right now that talks about happiness and how to achieve it in the modern…
Moderate Christians love to talk about how Jesus fixed the Old Testament, or, in other words, obsoleted the horribly offensive…
High quality intellectual output comes from high-quality intellectual input. People who don’t consume ideas tend not to have any. And…
Anyone who wishes to make advances in a particular intellectual area have essentially two options: Be an uber-deathgod-genius like Newton…
I don’t like salesishness, so let’s be clear about two things: I’m trying to get this site to where it…
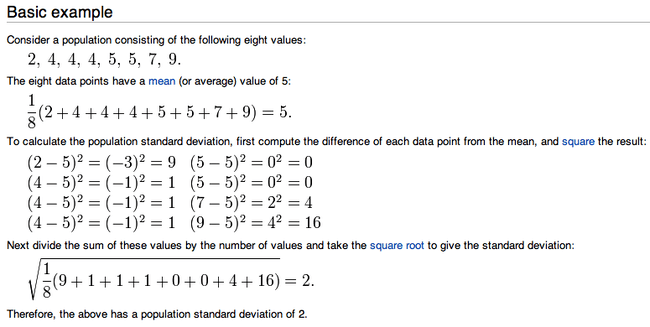
If you read a lot but aren’t much into math you’ve probably heard the term standard deviation being tossed around,…
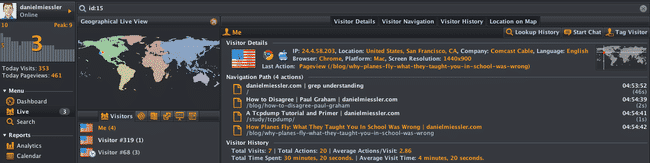
Something about realtime web analytics is just cool to me. I think it’s the idea of visualizing the interactions with…