Category: Mix
I’m a big fan of nmap‘s –top-ports option, which gives you the ability to leverage Fyodor’s latest Internet research on…
In response to this thread on Reddit: — Free will is a necessary delusion. The big bang happened, and then…
What follows is an excellent piece from Reddit on why leaving a religion can be so incredibly difficult. Here is…
62% of bankruptcies are from medical bills. Most medical debtors are well educated and middle class. Three quarters of those…
I have debated here at great length the degree of benefit or harm offered to society by religion. My position…
I saw this quote on Reddit recently, and it resonnated with me. It reminded me of my thoughts on meaning,…
For those not familiar, OpenID is a system that allows you to sign in to multiple websites using one identity….
I’ve noticed an ailment that a few of my male friends from the South have. This isn’t to say it’s…
Humans are notoriously poor at weighing risk. We use emotion, rather than reason, to judge what’s truly dangerous, which is…
So you have a Facebook account, right? And you use Google Mail, right? Good, then this is for you. It’s…
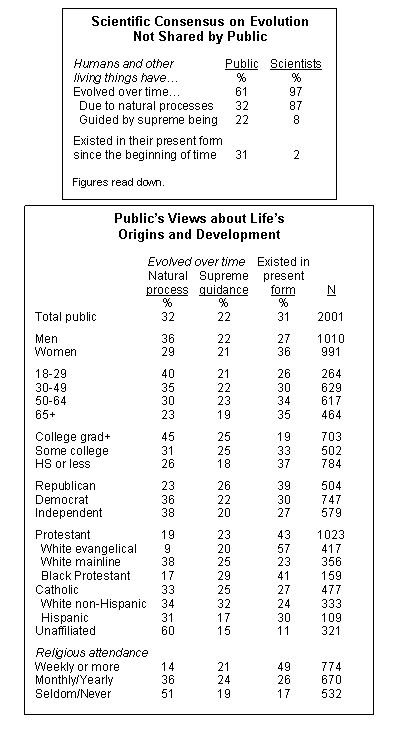
From a Pew poll. Image from Pew These numbers are simply staggering. It seems the trends are that as you…
You’ll want to check out this piece over at Less Wrong on fashion. It’s the clearest thinking I’ve ever seen…