Category: Mix
I think I’ve made a decision to be more direct in my attacks against beliefs in the supernatural (including religion)….
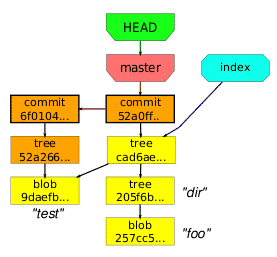
I’ve had a nagging problem for some time where I couldn’t figure out quite how to ignore my wp-content/cache directory…
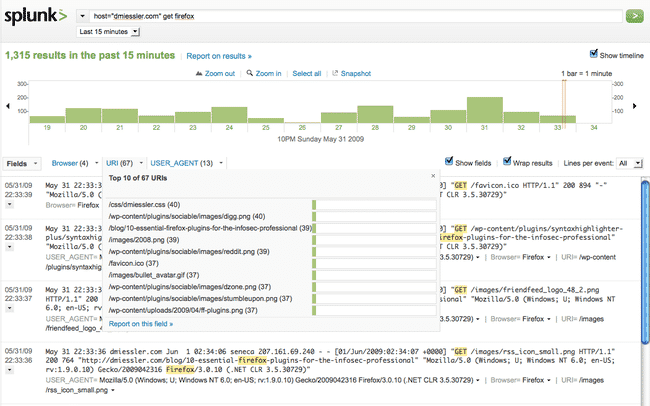
So I’ve been messing with Splunk> a bit recently, and as part of that I’ve been sending logs from iptables,…
I’ve written before about my issues with religious moderates who build their own religions by arbitrarily rejecting and embracing various…
I had an interesting idea last week about investing. The idea is that you get a bunch of experts in…
I’ve been debating here for quite some time the question of how direct, or even confrontational, to be with those…
My buddy at work asked me if I could find some location information for a list of IPs. I knew…
There is no supernatural origin of free will. All human action is the product of the interaction of a finite…
People struggle with why Twitter is special. It’s special because it counters, better than any other technology, the timeless social…
One of the most common arguments from the religious is that without God there would be no morality. Non-believers reject…
There are three fundamental ways of learning about the world, and they map well to concepts we’re all familiar with:…
It’s getting exciting in the world of cross-network authentication. Let’s review. I can now: We’re quickly approaching the point where…

![Religious Moderates Are Those Who Reject God’s Clearly Stated Commands Using Their Own [Human] Morality as Justification Religious Moderates Are Those Who Reject God’s Clearly Stated Commands Using Their Own [Human] Morality as Justification](https://image.cybernoz.com/wp-content/uploads/2025/04/Religious-Moderates-Are-Those-Who-Reject-Gods-Clearly-Stated-Commands.png)