Category: Mix
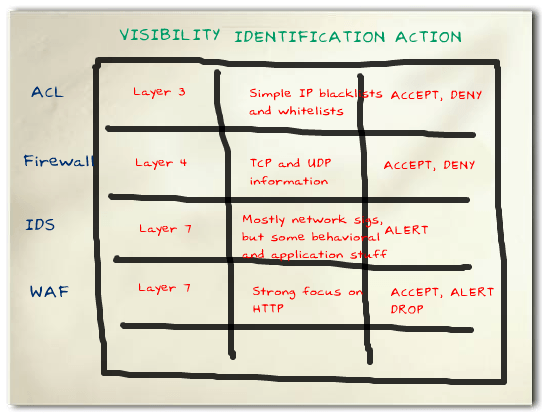
I inwardly smile when I hear the term “Unified Threat Management”. It means different things to different people, but to…
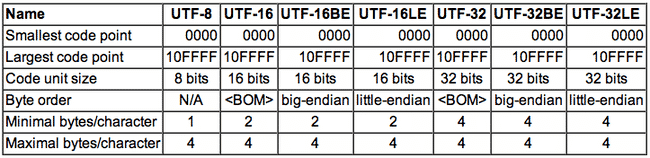
So everyone knows that UTF-8 encodes Unicode code points into eight bits, and UTF-16 encodes Unicode code points into 16…
A friend of mine (I’ll identify him if he so desires) sent me the following email: I think this is…
The über-tech-geek culture has a problem with tool obsession. Twitter, Friendfeed, Google Reader–these are all basics, but each of these…
This is an exciting protocol. I want to use it to get my various services’ content into Friendfeed, and to…
Scenario You have an Asterisk server behind a Check Point firewall trying to contact a VOIP provider located on the…
Evidently I’m not the only one who’s seeing what’s happening. I’ve been writing for years about how we’re approaching a…
I recently came up with a concept called Content Potential, which I define as the maximum level of popularity your…
Liberals love to blame poor Black and Hispanic performance in American public schools on the lack of school quality, e.g….
I’m often asked why I think so much of Quicksilver, and why it’s always part of my pitch when I’m…
I’ll mess this up, but here are the various ways we’ve been able to enjoy music throughout history: Live Vinyl…
Here’s a clean little summary of Ayn Rand’s book, Atlas Shrugged, from this Wall Street Journal article: Sound familiar yet?…