Category: Mix
Like many others, I’m trying to figure out where Twitter fits. Not just in my life online, but in general….
I’m seriously impressed with Google’s newbile browser offering, Chrome. I like the simplicity of its interface, its speed, and most…
One of the reasons people don’t want to leave Firefox for Google’s new Chrome Browser is Firefox’s Quicksearch feature, which…
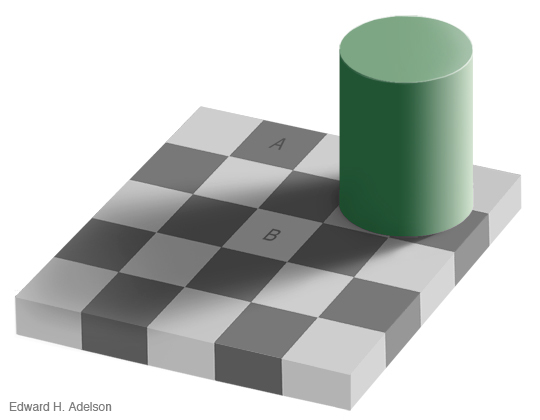
[ Published: Dec 26, 2008 ] A and B are exactly the same shade of gray. This essay is about…
I think if I were to have to guess, I would say that the reason we exist–or, to be more…
There are few things that help one’s efficiency more than being good with his preferred shell. Many know of the…
This post shows someone expressing disappointment with some future predictions given by Kurzweil back in 1999. Here they are as…
I have a problem. I am having serious trouble when faced with large, never-ending paperwork-based projects that require little to…
Many are wondering how OS X will fare against malware once it becomes a serious target. We won’t have to…
Anyone who likes Reddit needs to check out another similar site called Hacker News. It’s rather like Reddit used to…
A study has been released that says that talking on a mobile phone while driving is still very dangerous even…
Switch to Pure Key-based AuthenticationI say pure because it doesn’t help to just enable key-based authentication; you have to disable…