Category: Mix
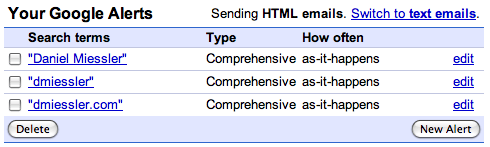
You don’t have to be an ego-freak to wonder if others are talking about you online. Egosurfing, i.e. the act…
Agentic AI is transforming business. Organizations are increasingly integrating AI agents into core business systems and processes, using them as…
A lingering feeling that I’ve had for roughly the last year was solidified for me last week at Blackhat/DEFCON. Making…
Ever wanted to take a piece of WordPress functionality and put it in a non-WordPress portion of your website? Like,…
I was getting into the elevator today, running back and forth between managing a long-term vendor project and keeping things…
This is for the people who believe in God, and believe in the power of prayer. The next time you…
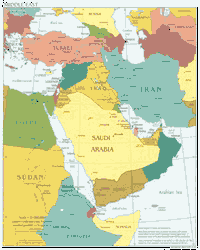
Most people–especially in the West–know very little about the Middle East and the people that live there. This lack of…
I made a prediction a couple months before the original iPhone came out that features would not be the deciding…
The Baader-Meinhof pheonomenon is kind of like Deja Vu in the sense that it’s something weird that many people have…
People often ask me why I choose to carry a concealed weapon. When I respond that there is real crime…
It’s no secret that most native Chinese see Africans, and blacks in general, as inferior. The dynamics of that sentiment…
Perhaps it’s really the conservatives who believe most in equality. Is that why they get so upset when people speak…