Category: Mix
The information security community is a relatively small one, and it remains so even on the Internet. It feels good…
I’ve been thinking a lot recently about the usefulness of risk assessment. A while back I had an interesting conversation…
Most in the information security community have heard of the “cold-boot” attack against encryption products that was recently released by…
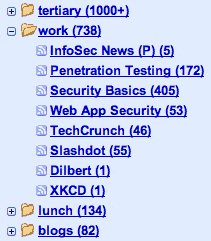
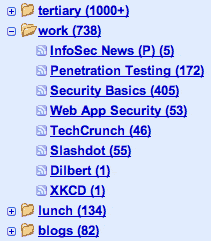
The fundamental problem when managing feeds is input management. Most of us simply have too many feeds to read in…
One of the most common arguments I hear from the religious is that their beliefs and mine are the same….
This explains a lot. The Dunning-Kruger effect describes the phenomenon whereby people who don’t know anything about something think they…
Subdomain takeovers are a well-documented security misconfiguration. Despite widespread awareness, developers still frequently forget to remove DNS records pointing to…
A new BBC piece is highlighting an alternate approach to depression. Rather than assume that it’s something that should immediately…
This is sickening. Fermilab, The United States’ main particle physics lab, is being hamstrung by congress’s latest omnibus bill. This…
I used to be into BMX bikes. I was obsessed. Every little thing about it was interesting. The brakes, the…
I’m constantly optimizing how I do things, and nowhere is this more important to me than with my feed reader….
I’m not an economist, but I read a lot. Here’s what happened: greed + stupidity. Greed on the part of…